How This QBot Banking Trojan Is Exploiting Window's Calculator With Malware

Malware spammers have been sending out emails that leverage a legitimate copy of the Windows Calculator app to sideload malware. This is yet another cunning ploy by cyber threat actors, however the victim would have to willingly go through several processes to fall prey to the QBot Banking Trojan scheme. Below, we will talk about the characteristics of this malware, and how it seeks to infect a victim's computer. In turn, this knowledge should help you recognize similar suspicious emailed malspam (malware spam).
As per our headline, threat actors are currently attempting to spread the Qbot malware by utilizing the known and trusted Windows Calculator app. The process from spam email with malware link to user infection would go something like below:
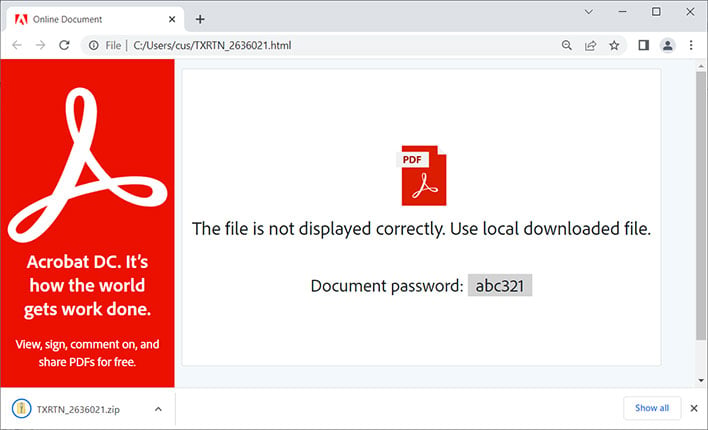
- User receives an unsolicited email which contains an .HTML file attachment.
- If the user clicks and opens the .HTML file, they are prompted to download a password protected .ZIP file.
- The .ZIP password is shared in the .HTML file, so the user can open and unpack it. Up until this time, any antivirus or anti-malware app won't have been able to scan the .ZIP contents.
- The unpacked archive contains an .ISO file which when opened by the user will mount a DVD image, revealing the contents.
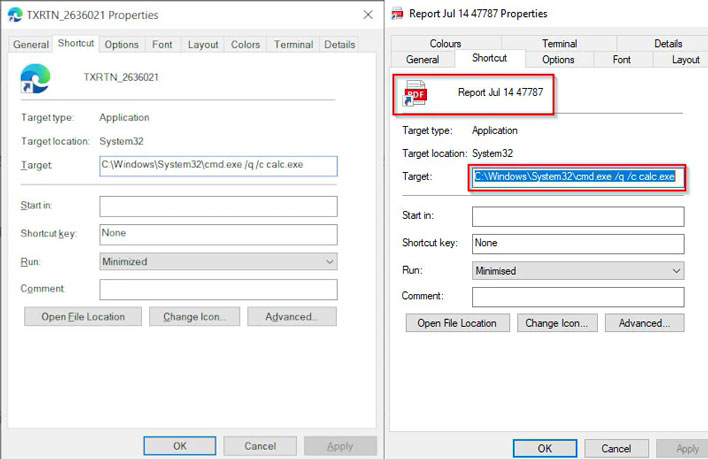
- Users are encouraged to open a .LNK shortcut file, which has been made to look like a .PDF document. However, as a Windows shortcut icon, it can run a chain of commands.
- If the user has followed the above steps, perhaps persuaded by some kind of social engineering, a command prompt opens, and they will be prompted to open Calc.exe.
- This is a genuine Calc.exe app, but from a Windows 7 distribution. Thus, it shouldn't trigger any antivirus reaction. However, the version of Calc.exe from Windows 7 has a vulnerability where it will sideload the .DLL files which reside in the DVD image beside it (this Vulnerability has been fixed in later versions of the calculator).
If a user has gone through all the above steps, they become vulnerable to multiple malware threats, including a number of 'popular' but unpleasant ransomware payloads. With ransomware, a threat actor will usually encryption lock user-files on the infected PC and demand payments for the unlock key.
There are quite a number of steps a victim must follow through, without getting too suspicious and halting their actions, for this malspam Trojan to be successful. Most experiences computer users will feel their spider senses tingling when faced with these emails in a very short period.
It would be interesting to know the success rate of the threat actor strategy of hiding the malware payload as a .DLL, to be sideloaded by Calc.exe. Would the basic minimum of Windows's built-in Defender antivirus and other security processes stop this in its tracks? Sadly, neither Bleeping Computer, nor security researcher ProxyLife, mention what AV solutions this malspam attack can swerve, if any.

