QBot Malware Hiding Inside Malicious Windows Installers Serves Up A Nasty Surprise

You might be thinking, 'Hey, I'm smart enough to know I shouldn't click on iffy links!', but that doesn't mean the tactic doesn't work. Developers of malware have known this for years, and this is frequently a preferred method of delivery for malware. Well, distributors of a well-known banking trojan, QBot, have decided to stop using one of its prolific distribution methods of "iffy Office attachments" and start sending people zip files with Windows Installers in them. Specifically MSI installers.
This is a new one. #qbot doing distro via password protected ZIP attachments with MSI's inside instead of your usual doc/xls/vbs/etc. Worth noting this and adjusting accordingly. Suspicions are that maybe the default changes for of XLM 4.0/VBA Macros rolling out is forcing hands. https://t.co/9r9T9TyBYX
— Joseph Roosen (@JRoosen) April 11, 2022
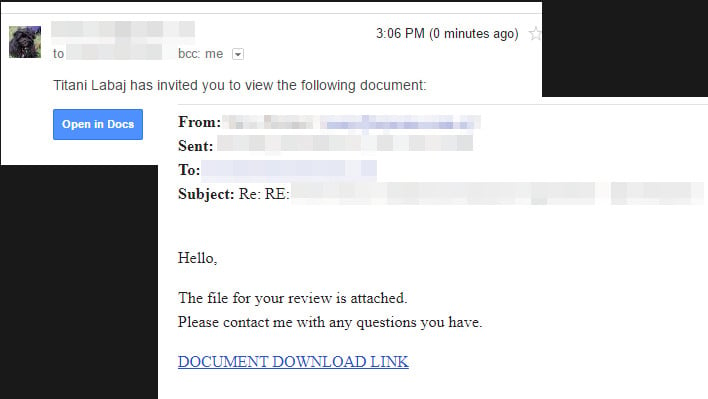
QBot, according to BleepingComputer, is most frequently used in efforts to affect large corporations. It is often the malware of choice for many ransomware groups as well, and because it can attack Active Directory admin accounts. It can also spread within networks. It is a particularly nasty piece of work. Some common methods of attack are also combined with what looks like legitimate e-mails from a spoofed version of a trusted contact. They can also look like a "secure file share", and they can even look like Google Drive, OneDrive, or DropBox file shares.