Ransomware Gang Built A Fake Cybersecurity Start-Up To Recruit Unwitting IT Specialists

The US government reported earlier this month that ransomware payments topped $81 million dollars in the first quarter of 2021 alone. This fact is in part the reason why the US government is looking to add new laws to combat ransomware. This also creates an environment where groups like Fin7 find creative ways of recruiting unknowing technology-minded workers to increase its ransomware income.
Fin7 has been responsible for exposing over 20 million payment card records, along with various ransomware attacks. The cybercriminal group is believed to be responsible for the recent ransomware attack on Colonial Pipeline back in May that stifled the flow of gasoline in the Southeastern states of the US. The group made its name in the mid-2010s for point-of-sale (POS) system attacks that included attacks on Saks Fifth Avenue and Lord & Taylor stores.
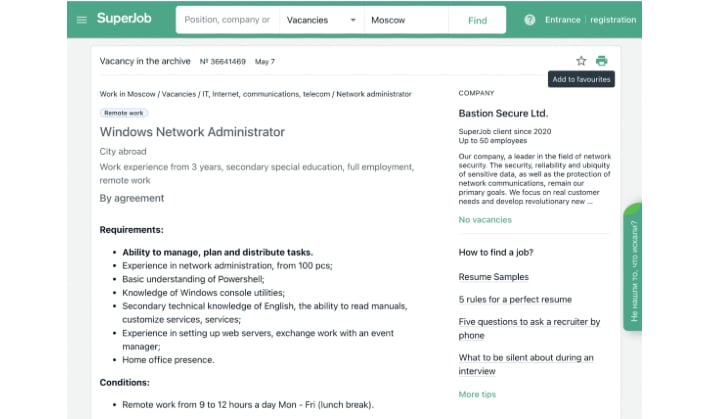
Gemini Advisory was able to infiltrate the group with a source that was recruited by the company, Bastion Secure. The company was used by Fin7 as a front to recruit and use unknowing workers for their cybercriminal empire. It allowed the group to pay the workers what appeared to be a fair wage, while pocketing the enormous profits of its true business at hand.
The job listing, aimed at IT specialists in post-Soviet states, led applicants to a business website that at first glance looked legitimate. In fact, the website was more or less a copy and paste of the site for Convergent Network Solutions Ltd. Applicants were met with three stages as they made their way through the hiring process.
The first two stages seemed to fall in line with most any other hiring processes, with an interview and then some practice assignments. The third stage introduced the applicants to a “real” assignment. They were given a “client company” to work on by Bastion Secure. This task included using a script to collect information on domain administrators, domain trust relationships, file shares, backups, and hypervisors. All of this should have thrown up red flags to most applicants.
This falls in line with how Fin7 has operated in the past with fake fronts. By using workers without knowledge of the true intent of the company, it was capable of securing a much larger portion of its profits. Whereas if the workers had knowledge of the operation (and low scruples), they surely would have demanded a much larger cut for themselves from the group's illicit gains.
Gemini Advisory has sent its findings to its clients, and also reported them to the appropriate authorities to the ransomware scheme. All findings have been corroborated by Microsoft’s presentation at Mandiant Cyber Defense Summit 2021.
As ransomware grows in popularity among the cybercrime community, there will no doubt be more ingenious ways of recruiting capable people, with or without knowledge of the intent, to create a larger profit margin. But as Gemini pointed out in its findings, the greed associated with those new techniques provided it with the “in” needed to expose the criminal activities behind Bastion Secure.