Ransomware Gang Releases Security Tool To Check If Your Data's Been Stolen, Gee Thanks

Ransomware is bad news not only because it can cause business-ending disruptions, as in the case of Abraham Lincoln College, but also because the actors behind ransomware attacks often exfiltrate data from compromised systems in addition to encrypting the data on said machines. Ransomware gangs tend to use this stolen data as an extra incentive for victims to pay the ransoms by threatening to release the stolen data on the web if the ransoms aren’t paid. The LockBit ransomware gang regularly employs this tactic, and threatened to release proprietary Foxconn data earlier this month after carrying out a ransomware attack on a Foxconn manufacturing plant.
A different ransomware gang known as ALPHV seems to be building on this tactic by testing out a new way to further incentivize its victims to pay ransoms. Ransomware gangs usually publish their threats on .onion sites that can be accessed only through the Tor network. These sites are part of the “dark web” and don’t appear in search results. By using .onion sites, the cybercriminals gain a level of anonymity that can’t be achieved anywhere else on the web. However, restricting access to the publication of their threats also limits the reach of their threats.
A different ransomware gang known as ALPHV seems to be building on this tactic by testing out a new way to further incentivize its victims to pay ransoms. Ransomware gangs usually publish their threats on .onion sites that can be accessed only through the Tor network. These sites are part of the “dark web” and don’t appear in search results. By using .onion sites, the cybercriminals gain a level of anonymity that can’t be achieved anywhere else on the web. However, restricting access to the publication of their threats also limits the reach of their threats.
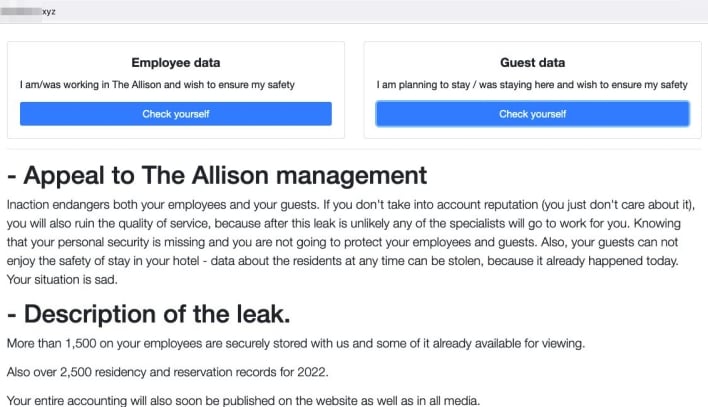
ALPHV has taken the unconventional approach of publicizing their recent breach of The Allison Inn & Spa to the “clearnet” and providing a tool where employees and guests of the business can check to see whether their information is included in the data stolen by the ransomware gang. The group released the tool on a website accessible to everyone without the use of Tor. However, as far as we can tell, the website has since been taken down, possibly by the host provider or the domain name service.
While the website presented itself as a useful security tool for potential victims to check whether their personal information was caught up in the ransomware attack, it’s a good thing the site has gone down. The website included a database of guests’ names, arrival dates, and stay costs, as well as employee’s names, Social Security Numbers, dates of birth, phone numbers, and email addresses. Visitors to the site could download individual “data packs” that contained all this information for each employee. This kind of open publication of data by a ransomware group poses a threat that .onion sites don’t, as search engines could have potentially indexed the website and its contents and exposed the stolen information in search results.
Thankfully, potential victims of this ransomware attack don’t need to turn to a tool offered by the attackers to determine whether their personal information may have been stolen. The Allison’s finance director, Lonny Watne, said in a statement that the business is currently notifying victims of the attack and offering them credit and identity monitoring services. “The security of the information in our care is one of our highest priorities, and we have already taken important steps to help prevent this from happening again.”
While the website presented itself as a useful security tool for potential victims to check whether their personal information was caught up in the ransomware attack, it’s a good thing the site has gone down. The website included a database of guests’ names, arrival dates, and stay costs, as well as employee’s names, Social Security Numbers, dates of birth, phone numbers, and email addresses. Visitors to the site could download individual “data packs” that contained all this information for each employee. This kind of open publication of data by a ransomware group poses a threat that .onion sites don’t, as search engines could have potentially indexed the website and its contents and exposed the stolen information in search results.
Thankfully, potential victims of this ransomware attack don’t need to turn to a tool offered by the attackers to determine whether their personal information may have been stolen. The Allison’s finance director, Lonny Watne, said in a statement that the business is currently notifying victims of the attack and offering them credit and identity monitoring services. “The security of the information in our care is one of our highest priorities, and we have already taken important steps to help prevent this from happening again.”

