Raspberry Robin Malware Caught Employing A Clever Tactic To Dupe Security Researchers

Earlier this year, researchers from the threat intelligence group Red Canary identified an infectious computer worm that was found to have been present in customers’ environments going back to September 2021. According to later analysis by Microsoft, this malware, which researchers named “Raspberry Robin,” may date as far back as 2019 and has since grown to integrate with a larger malware ecosystem. New research by Trend Micro has revealed an updated version of Raspberry Robin that began spreading through telecommunications and government systems in September. This new variant attempts to trick security researchers by obscuring its real payload and deploying a fake payload when it detects active security tools.
Cybersecurity analysts classify Raspberry Robin as a computer worm because it spread across systems in a self-replicating manner. This particular worm spreads by copying itself from an infected machine to any attached USB drives, then further infecting any machines that connect to those USB drives in the future. While spreading via USB drives can mean that Raspberry Robin doesn’t proliferate as quickly as worms that spread over the internet or local area network (LAN), this method of transmission makes Raspberry Robin dangerous in other ways. The worm can lie dormant on USB drives for extended periods, then re-infect computers that were cleaned of the malware. USB drive transmission also enables Raspberry Robin to cross air gaps and infect systems with no network access, including offline archives storing valuable information. Such an infection could be disastrous if the worm deploys data-destroying malware such as ransomware.
Researchers have observed Raspberry Robin deploying a variety of different malicious payloads, often as part of multi-stage infection chains that can end in the deployment of ransomware. According to Microsoft, this worm has evolved into one of the largest malware distribution platforms, and threat actors may even be paying the developers of Raspberry Robin to deploy particular payloads on infected machines. Thus, Raspberry Robin has come to play the role of a malware dropper, infecting computers for the purpose of installing additional malware.
Cybersecurity analysts classify Raspberry Robin as a computer worm because it spread across systems in a self-replicating manner. This particular worm spreads by copying itself from an infected machine to any attached USB drives, then further infecting any machines that connect to those USB drives in the future. While spreading via USB drives can mean that Raspberry Robin doesn’t proliferate as quickly as worms that spread over the internet or local area network (LAN), this method of transmission makes Raspberry Robin dangerous in other ways. The worm can lie dormant on USB drives for extended periods, then re-infect computers that were cleaned of the malware. USB drive transmission also enables Raspberry Robin to cross air gaps and infect systems with no network access, including offline archives storing valuable information. Such an infection could be disastrous if the worm deploys data-destroying malware such as ransomware.
Researchers have observed Raspberry Robin deploying a variety of different malicious payloads, often as part of multi-stage infection chains that can end in the deployment of ransomware. According to Microsoft, this worm has evolved into one of the largest malware distribution platforms, and threat actors may even be paying the developers of Raspberry Robin to deploy particular payloads on infected machines. Thus, Raspberry Robin has come to play the role of a malware dropper, infecting computers for the purpose of installing additional malware.
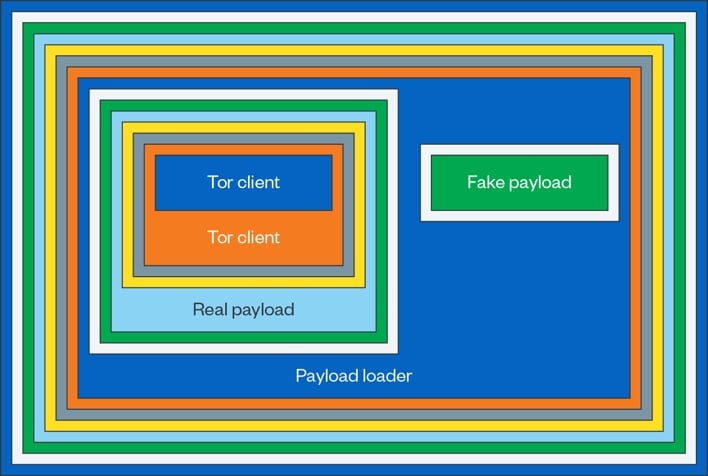
Unfortunately, it can be difficult for security researchers, let alone anti-virus software, to detect and identify Raspberry Robin. The worm’s infection chain begins with a .LNK shortcut file on a USB drive. Once the drive is connected to a Windows machine and a user double-clicks the shortcut, an executable file runs that instructs the legitimate msiexec.exe service to download and install a malicious .MSI Windows Installer package. This malicious package includes the bulk of the Raspberry Robin malware.
However, the malicious code is hidden behind over ten obfuscated layers. At runtime, each layer of the malware works to unpack and decrypt the next layer in sequence. When this process reaches the payload loader, the loader attempts to detect sandboxing and security analytics tools. If such tools are detected, the loader unpacks and loads a fake payload intended to mislead security researchers. This fake payload collects and exfiltrates system information before downloading and installing adware. Security researchers observing this behavior may be tricked into believing that they’ve determined the full extent of the malware’s activity.
However, when the payload loader determines that no sandboxing or security analytics tools are active, it unpacks and loads the real payload, which is significantly more malicious. It abuses user admin permissions to elevate its privileges, evade detection, and establish persistence on the infected system by editing the Windows registry. Further embedded within the real payload is a Tor client, which the malware uses to communicate with command-and-control (C2) servers controlled by the threat actors behind Raspberry Robin. Having established a backdoor to the infected system, the threat actors can then send additional malicious payloads for the malware to install and run.
This new variant of Raspberry Robin goes to show the lengths to which threat actors will go to develop malware that can hide from security researchers and anti-virus software. In order to avoid becoming the next victim of this worm and others like it, individual users and organizations alike should always remain vigilant and be cautious of opening unfamiliar files, even when they may appear harmless upon inspection.
However, the malicious code is hidden behind over ten obfuscated layers. At runtime, each layer of the malware works to unpack and decrypt the next layer in sequence. When this process reaches the payload loader, the loader attempts to detect sandboxing and security analytics tools. If such tools are detected, the loader unpacks and loads a fake payload intended to mislead security researchers. This fake payload collects and exfiltrates system information before downloading and installing adware. Security researchers observing this behavior may be tricked into believing that they’ve determined the full extent of the malware’s activity.
However, when the payload loader determines that no sandboxing or security analytics tools are active, it unpacks and loads the real payload, which is significantly more malicious. It abuses user admin permissions to elevate its privileges, evade detection, and establish persistence on the infected system by editing the Windows registry. Further embedded within the real payload is a Tor client, which the malware uses to communicate with command-and-control (C2) servers controlled by the threat actors behind Raspberry Robin. Having established a backdoor to the infected system, the threat actors can then send additional malicious payloads for the malware to install and run.
This new variant of Raspberry Robin goes to show the lengths to which threat actors will go to develop malware that can hide from security researchers and anti-virus software. In order to avoid becoming the next victim of this worm and others like it, individual users and organizations alike should always remain vigilant and be cautious of opening unfamiliar files, even when they may appear harmless upon inspection.

