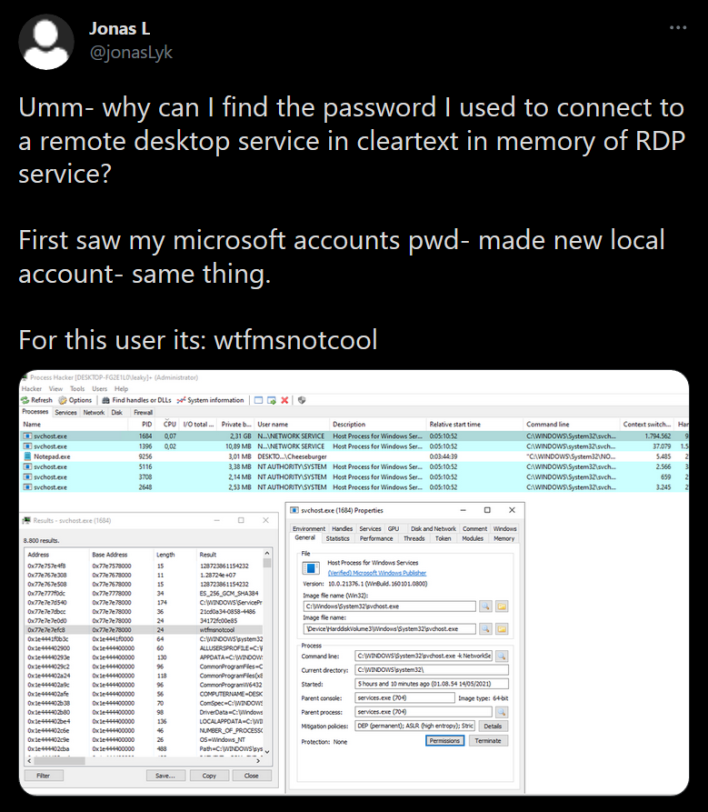
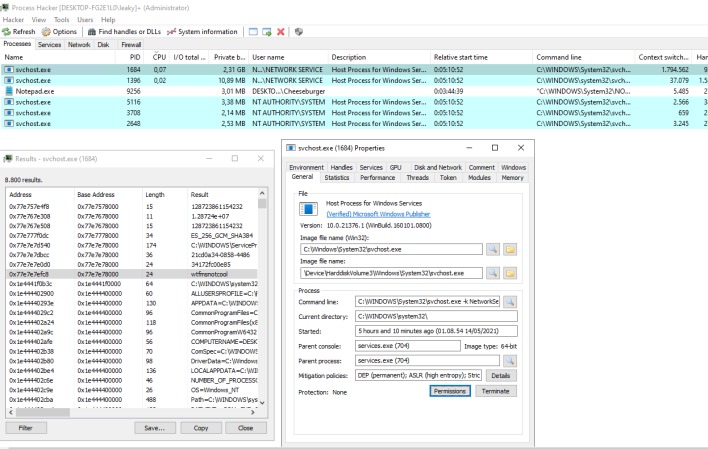
Microsoft Remote Desktop Protocol (RDP) Allegedly Has An Alarming Active Vulnerability

The Remote Desktop Protocol (RDP) is an incredibly useful feature used by likely millions of people every day. Considering it is free and preinstalled from Microsoft, it beats out most other Windows-based remote desktop software with ease. This, however, does not give it a free pass from having flaws; however, as a security researcher has discovered his password in cleartext within the RDP service’s memory.
Researcher Jonas Lykkegård of the Secret Club, a group of hackers, seems to stumble across interesting things from time to time. He recently posted to Twitter about finding a password in cleartext in memory after using the RDP service. It seems he could not believe what he had found, as he tested it again and produced the same results using a new local account.