Dark Day For Smart Light Bulbs As Researchers Discover TP-Link Security Threat

The first and most severe vulnerability discovered involves a lack of authentication between the smart bulb and its companion app. This vulnerability has a high-severity 8.8 out of 10 score on the Common Vulnerability Scoring System (CVSS) and works because anyone could authenticate to the Tapo app pretending to be the smart bulb. The second vulnerability has a 7.6 CVSS score and stems from a hard-coded secret used by both the Tapo app and the smart bulb, which is exposed by code fragments used by both.

Vulnerability three has a lower 4.6 CVSS score and is concerned with a lack of randomness during symmetric encryption. The fourth and final vulnerability has a 5.7 CVSS score and notes that neither the app nor the smart bulb have a means to check the freshness of the message received, essentially implying replay attacks. While all these separately are not of utmost concern, you can put the vulnerabilities together to yield some interesting results.
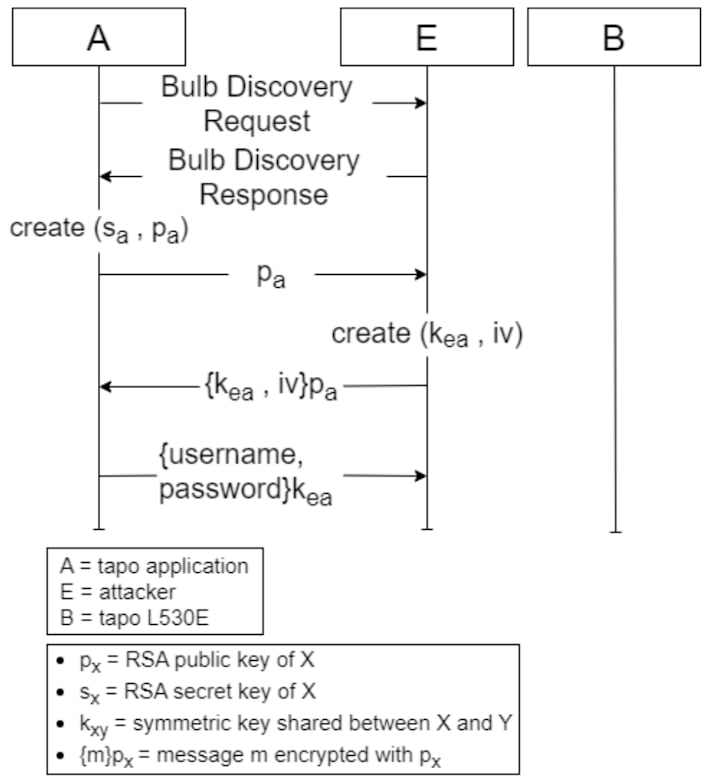
The researchers found that an attacker could exploit vulnerabilities one and two to get the password and hashed email of the victim’s Tapo account. In theory, the attacker could also get Wi-Fi credentials for the network that the smart bulb is on, meaning that they could pivot to other devices once connected to the network.
Of course, there are numerous other ways to exploit these vulnerabilities that the researchers were not able to cover in their paper (PDF). Thankfully, though, these issues were reported to TP-Link, who acknowledged them and reported that it would be working on fixes. Despite this, this does validate long-standing concerns about insecure IoT devices being introduced to people’s homes.
As such, it is recommended to keep IoT devices on a separate network altogether while also following best practices; per CISA, check security settings on your devices, keep software up to date, use strong passwords, and connect things to the internet only if absolutely necessary.

