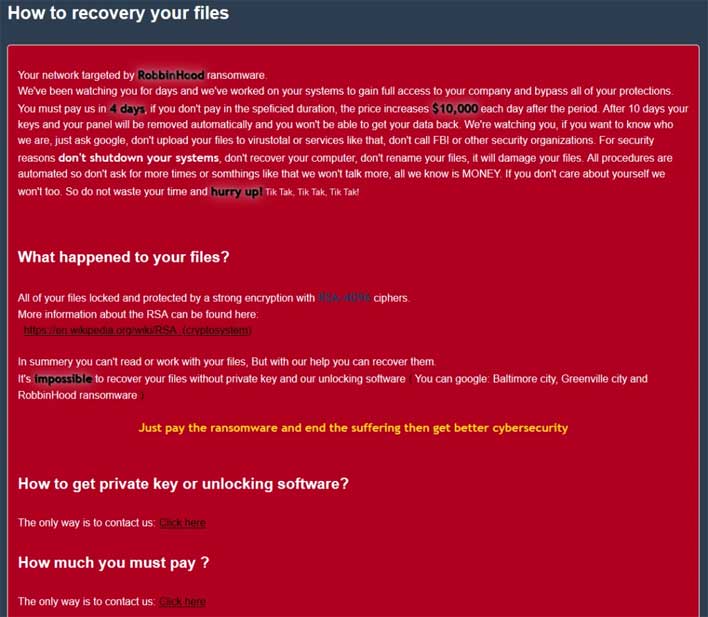
Cunning RobbinHood Ransomware Employs Gigabyte Hardware Driver To Hold Data Hostage
Security researchers at Sophos have been investigating a pair of ransomware attacks where the attackers used legitimate, digitally signed hardware driver to delete security products from targeted computers. Once the security products were deleted from the target machines, the destructive file encryption portion of the attack was launched. The signed driver that was used is part of a deprecated software package from Gigabyte, a mainboard and computer hardware manufacturer.
The software had a known vulnerability tracked as CVE-2018-19320. The vulnerability, along with proof-of-concept code was published in 2018. At the time, Gigabyte denied that the vulnerability impacted its products. Later it admitted there was a vulnerability and stopped using the software, but there are still vulnerable computers out there the RobbinHood ransomware targets.
The driver exploited in the attack was signed using Verisign. The company hasn't revoked the signing certificate meaning the Authenticode signature is valid. The attackers used the Gigabyte driver as a wedge so they can load a second, unsigned driver into Windows. That second driver kills processes and files that belong to security products and bypasses tamper protection. That allows the ransomware to attack without interference from security products.
Sophos says that this is the first time that it has observed ransomware shipping a trusted, signed, but vulnerable driver and then loading an unsigned malicious driver for its attack. Ransomware side-stepping security software isn't new. Sophos is taking a deep dive into the malware, which can be seen here, and says that it is doing so to allow defenders to anticipate and enact defenses against the attack.
To prevent the attack from happening, Sophos suggests some mitigation techniques. It says that administrators should deploy a range of technologies to disrupt as many stages of attack as possible. Users should have strong security practices like MFA, complex passwords, limited access rights, and make regular backups, among other things. Admins also need to educate staff; Sophos points out that people are the weakest link in cybersecurity.
As costly as cyberattacks are for businesses who lose data and productivity, there is a much more sinister side to ransomware attacks. Researchers linked a rise in fatal heart attacks to hospital ransomware attacks late in 2019. The increase in deaths was related to the extra wait time for treatments after a ransomware attack.