How Russian Code Infiltrated Android And iOS Apps Used By The CDC And US Army

Around 8,000 Android and iOS apps rely on code provided by Pushwoosh to monitor user activity and send custom push notifications. According to a report by Reuters, Pushwoosh has made efforts to portray itself as a US-based company, obscuring the fact that the company operates out of Russia. Among the clients that included Pushwoosh’s code in their apps are the Centers for Disease Control and Prevention (CDC) and US Army. Both organizations have since removed this code from their apps, citing deception on the part of Pushwoosh and national security concerns.
Mobile app developers often rely on third-party pre-packaged code that provides specific functionality. This code comes in the form of a software development kit, or SDK for short, and many apps include multiple SDKs. Pushwoosh is a company that develops and distributes one such SDK. The Pushwoosh SDK registers users and tracks their behavior, including precise geolocation data, for the purposes of collecting usage statistics and sending custom push notifications tailored to users’ activity.
Pushwoosh also handles storing and processing all the data collected from the apps containing its SDK. Given the potentially sensitive user information gathered by Pushwoosh, the company’s identity and location are important pieces of information for those considering whether to integrate the Pushwoosh SDK into their apps. However, Pushwoosh seems to have obscured this information with conflicting claims.
Mobile app developers often rely on third-party pre-packaged code that provides specific functionality. This code comes in the form of a software development kit, or SDK for short, and many apps include multiple SDKs. Pushwoosh is a company that develops and distributes one such SDK. The Pushwoosh SDK registers users and tracks their behavior, including precise geolocation data, for the purposes of collecting usage statistics and sending custom push notifications tailored to users’ activity.
Pushwoosh also handles storing and processing all the data collected from the apps containing its SDK. Given the potentially sensitive user information gathered by Pushwoosh, the company’s identity and location are important pieces of information for those considering whether to integrate the Pushwoosh SDK into their apps. However, Pushwoosh seems to have obscured this information with conflicting claims.
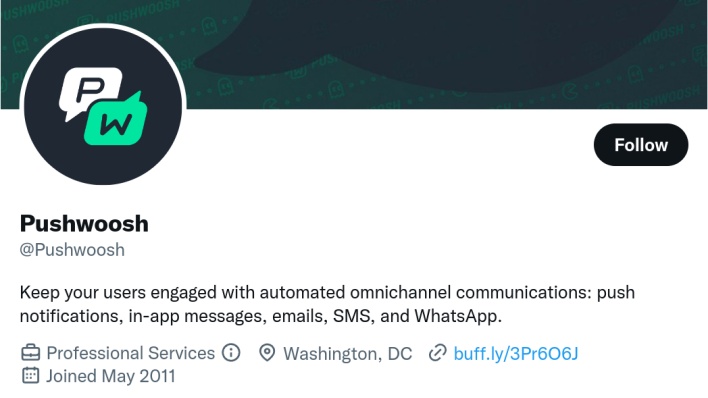
The company’s recent regulatory filings submitted to Delaware’s secretary of state list a house in Kensington, Maryland as its office of address. In previous filings from 2014 to 2016, Pushwoosh claimed to operate from an address in Union City, California. Meanwhile, the Pushwoosh’s Twitter profile displays Washington, D.C. as the company’s location. Reuters also found that the company solicited sales using two LinkedIn accounts that appeared to belong to company executives based in Washington, D.C.
As it turns out, Pushwoosh is registered with the Russian government as a software company headquartered in Novosibirsk, where around forty employees carry out their work. The house in Maryland listed on the company’s regulatory filings belongs to a Russian friend of Max Konev, the founder of Pushwoosh. The owner of the house told Reuters that he had nothing to do with Pushwoosh and simply agreed to allow the company to receive mail at his address. According to Konev, this arrangement to “receive business correspondence” at his friend’s house began during the COVID-19 pandemic.
Konev also told Reuters that the company’s new location of operation is in Thailand. However, Reuters received no evidence to support this claim and was unable to find a Pushwoosh in Thailand’s company registry. Reuters was able to determine that the two executives living in Washington, D.C., Mary Brown and Noah O’Shea, are not real people, but rather fabrications created on LinkedIn. The picture displayed on Mary Brown’s profile is actually a picture taken by a photographer in Moscow, Russia of a dance teacher who lives in Austria. Reuters contacted the teacher, who said she didn’t know how her picture wound up on LinkedIn.
After confirming the LinkedIn profiles as fake, Konev told Reuters that a marketing agency hired by Pushwoosh in 2018 created the accounts in a social media campaign to sell Pushwoosh. Konev stated that the accounts were not created to hide the fake that Pushwoosh is based in Russia. To the contrary, Konev told Reuters, “I am proud to be Russian and I would never hide this.” Nonetheless, Pushwoosh has never acknowledged that it is a Russian-based company in any of its eight annual filings with the Delaware secretary of state. By failing to acknowledge this fact, Pushwoosh may have both violated state law and deceived its clients.
As it turns out, Pushwoosh is registered with the Russian government as a software company headquartered in Novosibirsk, where around forty employees carry out their work. The house in Maryland listed on the company’s regulatory filings belongs to a Russian friend of Max Konev, the founder of Pushwoosh. The owner of the house told Reuters that he had nothing to do with Pushwoosh and simply agreed to allow the company to receive mail at his address. According to Konev, this arrangement to “receive business correspondence” at his friend’s house began during the COVID-19 pandemic.
Konev also told Reuters that the company’s new location of operation is in Thailand. However, Reuters received no evidence to support this claim and was unable to find a Pushwoosh in Thailand’s company registry. Reuters was able to determine that the two executives living in Washington, D.C., Mary Brown and Noah O’Shea, are not real people, but rather fabrications created on LinkedIn. The picture displayed on Mary Brown’s profile is actually a picture taken by a photographer in Moscow, Russia of a dance teacher who lives in Austria. Reuters contacted the teacher, who said she didn’t know how her picture wound up on LinkedIn.
After confirming the LinkedIn profiles as fake, Konev told Reuters that a marketing agency hired by Pushwoosh in 2018 created the accounts in a social media campaign to sell Pushwoosh. Konev stated that the accounts were not created to hide the fake that Pushwoosh is based in Russia. To the contrary, Konev told Reuters, “I am proud to be Russian and I would never hide this.” Nonetheless, Pushwoosh has never acknowledged that it is a Russian-based company in any of its eight annual filings with the Delaware secretary of state. By failing to acknowledge this fact, Pushwoosh may have both violated state law and deceived its clients.

Multiple CDC apps that sent health-related notifications to users contained the Pushwoosh SDK, but the organization removed the SDK after it was made aware of the company’s true location of operation. According to a CDC spokesperson, Kristen Nordlund, “CDC believed Pushwoosh was a company based in the Washington, D.C. area.” However, despite using the Pushwoosh SDK, the CDC claims that it “did not share user data with Pushwoosh.”
In March of this year, the US Army ceased using an app containing the Pushwoosh SDK, citing “security issues.” The app in question was an information portal used by troops at the Fort Irwin National Training Center. Bryce Dubee, a spokesperson for the US Army, stated that the app did not connect to the Army network and its use did not result in any “operational loss of data.”
Other organizations and companies told Reuters that they have removed the Pushwoosh SDK from their apps since discovering Pushwoosh to be a Russia-based company. While the company’s founder denied any connection between the Russian government and Pushwoosh, the fact that the company’s SDK collects user behavior data and stores it on servers under the control of a company located in Russia raises concerns. Like China, the Russian government seems to have no qualms about forcing local companies to hand over user data.
In March of this year, the US Army ceased using an app containing the Pushwoosh SDK, citing “security issues.” The app in question was an information portal used by troops at the Fort Irwin National Training Center. Bryce Dubee, a spokesperson for the US Army, stated that the app did not connect to the Army network and its use did not result in any “operational loss of data.”
Other organizations and companies told Reuters that they have removed the Pushwoosh SDK from their apps since discovering Pushwoosh to be a Russia-based company. While the company’s founder denied any connection between the Russian government and Pushwoosh, the fact that the company’s SDK collects user behavior data and stores it on servers under the control of a company located in Russia raises concerns. Like China, the Russian government seems to have no qualms about forcing local companies to hand over user data.

