Scammers Pickpocketed $500K From Crypto Wallets By Dropping Phish Hooks In Google Ads

Do you ever forget to type the TLD (like, ".com") for websites that you visit, then click the top result when the inevitable search comes up? We might recommend you to stop doing that in the future. At least on Google and Bing, the first few results are advertisements, and those advertisements might not be as safe as their hosts would like you to think.
Check Point Research (CPR) has documented a new tactic in the endless war against cyber-criminals: buying Google ads. Crypto wallet users looking for popular apps like Phantom App and MetaMask have been targeted by cyber-criminals purchasing Google ads that link to their fake websites, and they look like very much like the real thing. Users that log into the fake site hand their credentials over to the thieves on a silver platter.
Even worse, if the unwitting crypto trader makes a new wallet using the fake site, they'll find that upon logging into the wallet in the future, they'll actually be logging into the bad guy's wallet, who will thereupon receive any currency transferred to that wallet. The MetaMask version of the bad actors' traps actually includes the ability to import existing wallets; doing so hands over the seed phrase for that wallet.
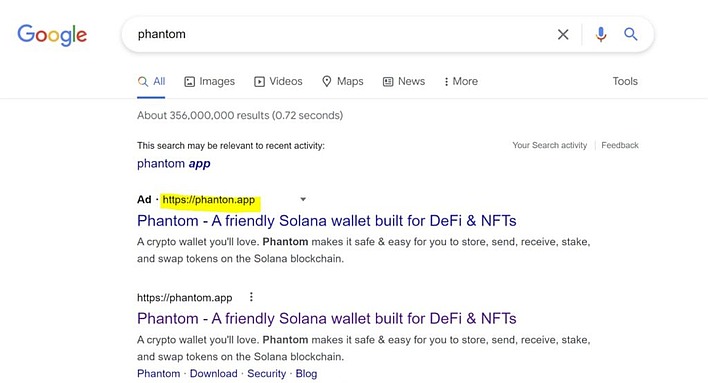
The security group goes on to say that these new phishing campaigns utilizing Google ads aren't the work of one actor, but of numerous agents or groups that compete with each other. They aren't just targeting Phantom and MetaMask, either; CPR points out that other popular crypto apps like PancakeSwap, UniSwap, and SushiSwap have been targeted, too.
Still, aside from the attack vector (Google ads), these phishing scams are pretty standard, so you can protect yourself with the usual methods of defending against phishing scams: always check the exact spelling of the URL, always make sure your connection is secure, and use bookmarks or shortcuts whenever you can to avoid typographical errors (or fraudulent advertisements).

