Schoolyard Bully Android Malware Wants Your Facebook Login, Not Your Lunch Money

The cybersecurity firm Zimperium, has published a blog post detailing a recently discovered Android malware campaign that has been ongoing since 2018. This campaign spreads a set of malicious apps the researchers are calling the “Schoolyard Bully Trojan” on account of the fact that the malicious apps are disguised as educational apps offering a wide range of books for users to read. However, rather than trying to steal your lunch money with banking malware, the Schoolyard Bully Trojan is out to swipe users’ Facebook account credentials. That said, as we’ll discuss, this effort may be a ploy to access victims’ financial accounts after all.
According to the researchers’ findings, this Trojan primarily targets Vietnamese users. However, the over 300,000 victims of this malware are spread across at least seventy-one countries, so this malware campaign still poses a threat to users outside of Vietnam. Zimperium researchers identified numerous apps on the Google Play Store that contained the Schoolyard Bully payload. Google has since removed these apps from the Play Store, but they are still available on third-party app stores for unsuspecting users to download.
According to the researchers’ findings, this Trojan primarily targets Vietnamese users. However, the over 300,000 victims of this malware are spread across at least seventy-one countries, so this malware campaign still poses a threat to users outside of Vietnam. Zimperium researchers identified numerous apps on the Google Play Store that contained the Schoolyard Bully payload. Google has since removed these apps from the Play Store, but they are still available on third-party app stores for unsuspecting users to download.
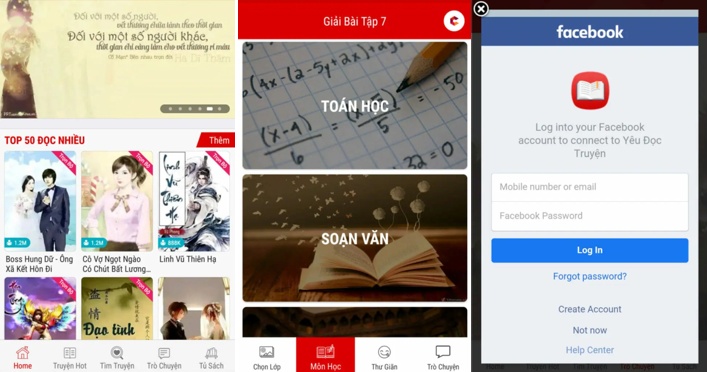
These fraudulent educational apps include what is presented as a chat feature that integrates with Facebook. When users select the chat tab, the apps present users with the legitimate Facebook login page. However, rather than rendering this webpage with Android System WebView, the apps instead use a custom in-app web browser that injects malicious JavaScript into the webpage. This code extracts any login credentials entered into the page and sends them to a server controlled by the threat actors behind this malicious campaign.
In a dark twist, Meta was caught earlier this year using a custom in-app browser within the Facebook, Instagram, and Messenger apps to inject what appeared to be a tracking script into webpages viewed within these apps. We wrote at the time of this discovery that it raised broader privacy and security concerns, as malicious apps could potentially use this same technique to inject code that steals login credentials. As it turns out, at least one malware campaign has been doing exactly as we speculated since 2018.
Zimperium also points out that this effort to steal Facebook login credentials may be part of a larger attempt to gain unauthorized access to victims’ bank accounts. People commonly re-use passwords across multiple accounts, as is shown by the effectiveness of credential stuffing attacks. Thus, distributing malware that subtly steals Facebook login credentials may be a more reliable method for gaining unauthorized access to users’ financial accounts than distributing banking malware, which typically requires that users grant it extensive permissions before it can be effective. When users don’t use unique passwords for each of their accounts, they shouldn’t assume that an attack on one account ends there.
In a dark twist, Meta was caught earlier this year using a custom in-app browser within the Facebook, Instagram, and Messenger apps to inject what appeared to be a tracking script into webpages viewed within these apps. We wrote at the time of this discovery that it raised broader privacy and security concerns, as malicious apps could potentially use this same technique to inject code that steals login credentials. As it turns out, at least one malware campaign has been doing exactly as we speculated since 2018.
Zimperium also points out that this effort to steal Facebook login credentials may be part of a larger attempt to gain unauthorized access to victims’ bank accounts. People commonly re-use passwords across multiple accounts, as is shown by the effectiveness of credential stuffing attacks. Thus, distributing malware that subtly steals Facebook login credentials may be a more reliable method for gaining unauthorized access to users’ financial accounts than distributing banking malware, which typically requires that users grant it extensive permissions before it can be effective. When users don’t use unique passwords for each of their accounts, they shouldn’t assume that an attack on one account ends there.

