Security Report Sounds Alarm On Evolving Android Malware Droppers In Google Play

Researchers at the threat analysis company ThreatFabric have published a report detailing some recent evolutions in Android malware droppers on the Google Play Store. Recent changes to Google Play policies restricting access to certain permissions have pushed malware developers to find workarounds. Google is constantly working to detect malicious applications and prevent them from appearing on its app stores where unsuspecting users could install them and unknowingly infect their own devices. However, crafty malware developers continually develop new ways to sneak malicious applications onto official app stores.
One established method for achieving this end is the use of malware droppers, which are applications that contain very little malicious code when first installed. Droppers usually masquerade as legitimate apps with useful features and often do offer at least some of the advertised functionality. However, once installed, malware droppers download and install malicious payloads. Since the droppers themselves don’t contain the bulk of the malicious code, but instead download it from external sources, it’s more difficult to detect the droppers as malicious. Earlier this week, we wrote about a family of extensions in the Chrome Web store that employed similar tactics to Android malware droppers, downloading and side-loading a set of malicious scripts from a blank webpage.
One established method for achieving this end is the use of malware droppers, which are applications that contain very little malicious code when first installed. Droppers usually masquerade as legitimate apps with useful features and often do offer at least some of the advertised functionality. However, once installed, malware droppers download and install malicious payloads. Since the droppers themselves don’t contain the bulk of the malicious code, but instead download it from external sources, it’s more difficult to detect the droppers as malicious. Earlier this week, we wrote about a family of extensions in the Chrome Web store that employed similar tactics to Android malware droppers, downloading and side-loading a set of malicious scripts from a blank webpage.
Android malware droppers tend to make use of the REQUEST_INSTALL_PACKAGES permission, which enables an app to issue a prompt asking users to grant the app the ability to install packages. Malware droppers abuse this permission to gain the ability to side-load malicious payloads. However, back in May of this year, Google announced an upcoming change to its Google Play policies, restricting access to this permission. That change went into effect at the end of September and requires that sending, receiving, and installing packages must be part of an app’s core functionality in order to access the REQUEST_INSTALL_PACKAGES permission.
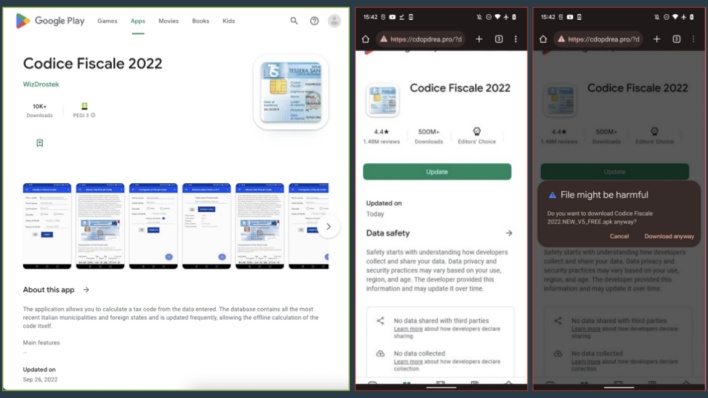
The new policy is intended to prevent malware droppers from abusing this permission by restricting access to the permission to exclusively apps like web browsers, file managers, and dedicated app stores. However, malware developers appear to have discovered at least two different ways to work around this restriction. ThreatFabric found the first of these two techniques at play in a Sharkbot malware dropper.
Rather than attempting to install the Sharkbot payloads itself, the malware dropper instead opens a webpage in the user’s default web browser. This webpage is designed to look like the Google Play Store and displays a fake update to the dropper app. Since web browsers can still access the REQUEST_INSTALL_PACKAGES permission under the new Play Store policy, the web browser can download and install the “update” at the direction of unsuspecting users. Users who carry out this update process to completion will have unwittingly infected their devices with the Sharkbot malware.
The new policy is intended to prevent malware droppers from abusing this permission by restricting access to the permission to exclusively apps like web browsers, file managers, and dedicated app stores. However, malware developers appear to have discovered at least two different ways to work around this restriction. ThreatFabric found the first of these two techniques at play in a Sharkbot malware dropper.
Rather than attempting to install the Sharkbot payloads itself, the malware dropper instead opens a webpage in the user’s default web browser. This webpage is designed to look like the Google Play Store and displays a fake update to the dropper app. Since web browsers can still access the REQUEST_INSTALL_PACKAGES permission under the new Play Store policy, the web browser can download and install the “update” at the direction of unsuspecting users. Users who carry out this update process to completion will have unwittingly infected their devices with the Sharkbot malware.
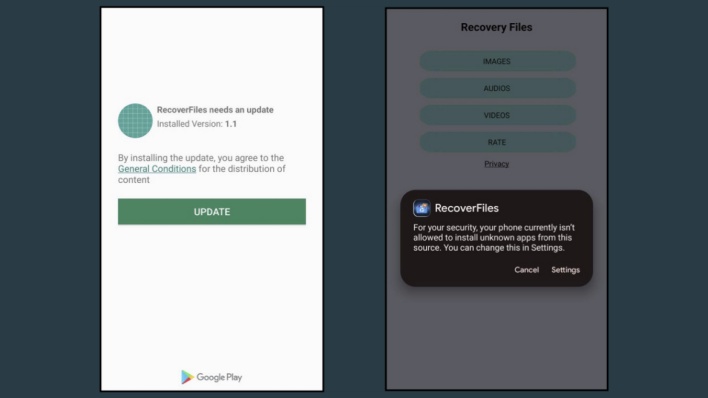
ThreatFabric also discovered a second workaround employed by both a different Sharkbot dropper and a dropper for the Vultur malware. Under the new Play Store policy, file managers are still allowed to access the REQUEST_INSTALL_PACKAGES permission, and malware developers can take advantage of this allowance by creating malware droppers that masquerade as legitimate file manager apps. These malicious file manager apps can then display a fake update screen and directly request the ability to install packages. If users grant this ability to the malware droppers, they can promptly install malicious payloads.
Android users should always be hesitant to grant apps the ability to install packages. As a general rule of thumb, this setting should be enabled only for trusted, dedicated app stores. Users should also be aware that the real Google Play Store will never request access to this ability, as it is granted by default.
Android users should always be hesitant to grant apps the ability to install packages. As a general rule of thumb, this setting should be enabled only for trusted, dedicated app stores. Users should also be aware that the real Google Play Store will never request access to this ability, as it is granted by default.