Security Report Details Alarming Rise In Malware Attacks Using USB Drives

Earlier this week, researchers at Mandiant reported that they had observed a tripling of the number of attacks using infected USB drivers over the first half of 2023. In this growth, two major espionage campaigns that utilized malicious USBs were tracked, dubbed SOGU and SNOWYDRIVE, respectively. The former, SOGU, is reportedly one of the most prevalent and aggressive espionage campaigns targeting public and private sector organizations globally.
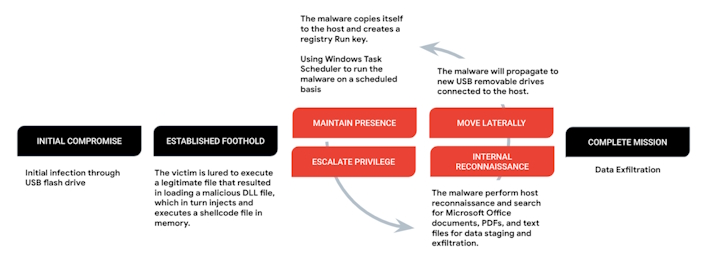
The SOGU operation begins with an infected flash drive containing malicious software that aims to load a payload to memory using DLL hijacking. Per the report, the infection chain that comprises this attack typically has three files, a legitimate executable, a malicious DLL loader, and an encrypted payload. A user who finds the USB must run the executable on the USB to load the malicious DLL dubbed ‘KORPLUG.’ This DLL will load shellcode, dubbed ‘SOGU,’ into memory. This shellcode collects some information, stages Office documents and PDFs for exfiltration, and sets up persistence masquerading as a legitimate program. The staged data is then exfiltrated using any number of different protocols, including custom ones, after which the malware could potentially clone itself to new drives plugged into an infected system.
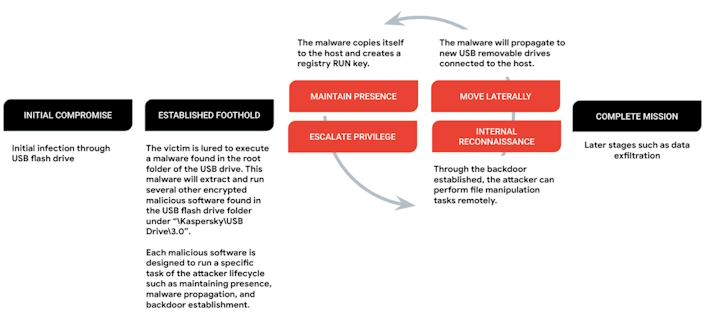
SNOWYDRIVE is very similar but operates by tricking a user into running a malicious file that looks like a legitimate executable on the drive. This malicious file is a dropper that pulls down and runs other malware on disk. This second stage of malware can then pull and run a shellcode-based backdoor, avoid AV detection, infect other flash drives, and more. The backdoor also generates a unique identifier and will communicate with the attacker’s command and control (C2) infrastructure.
Mandiant explains that with both attacks, “local print shops and hotels [are] potential hotspots for infection.” However, the threat actors are not specifically targeting these industries and are acting more opportunistically. Therefore, as Mandiant suggests, organizations should work to implement restrictions on USB drivers or otherwise scan all external devices for malicious files or code before granting access. You never know when a parking lot USB will bring you trouble.

