Sega Left A Massive User Database Vulnerable But It Could Have Been Worse

It's a good idea for big organizations to hire security researchers for help securing their systems. No matter how much effort you put into something (like securing your network), it can sometimes require a person looking at it from a different angle to point out a problem you couldn't see.
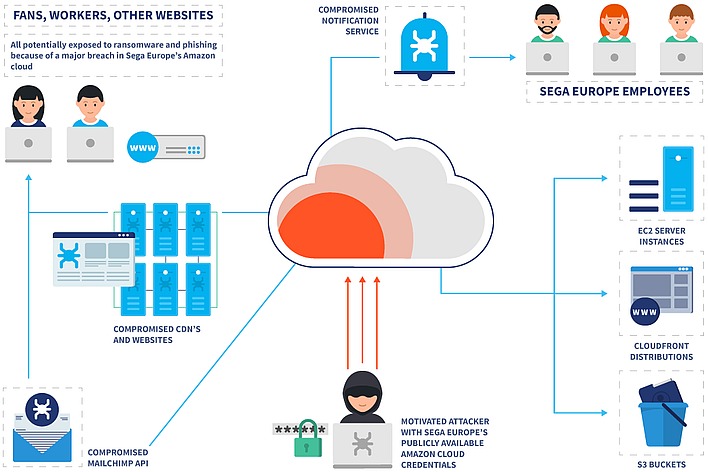
Given that lede and headline, you probably won't be surprised when we tell you that Sega Europe hired VPN Overview to run a little security check and found that the house of Sonic the Hedgehog was stashing all kinds of sensitive data in a publicly-accessible Amazon bucket. The bucket contained Keys for Sega's MailChimp and Steam accounts, as well as access to multiple content delivery networks.
Using the data in the AWS bucket, a malicious actor could have caused all kinds of havoc: changes to Sega's games on Steam, falsified (yet completely official-looking) e-mails from Sega, illicit SNS notifications, and other such misdeeds. The bucket also contained some user data, including "information on hundreds of thousands of users of the Football Manager forums."
Furthermore, the AWS keys allowed "read and write access to Sega Europe's cloud storage." Sega hosts many of its websites on Amazon servers, and using the information in the compromised bucket, researchers could have uploaded files, executed scripts, altered existing web pages, and modified the server configuration of vulnerable Sega sites.
Fortunately, none of that happened, and it's all because Sega got lucky that nobody found the security hole before VPN Overview. Indeed, there's no evidence at all that anyone even found the hole in Sega Europe's network, much less exploited it, so if you're a Football Manager addict, don't worry—your data is safe with Sega... for now, anyway.