Cybercriminals Spend 11 Days On Average Embedded Within Vulnerable Networks Before Attacking

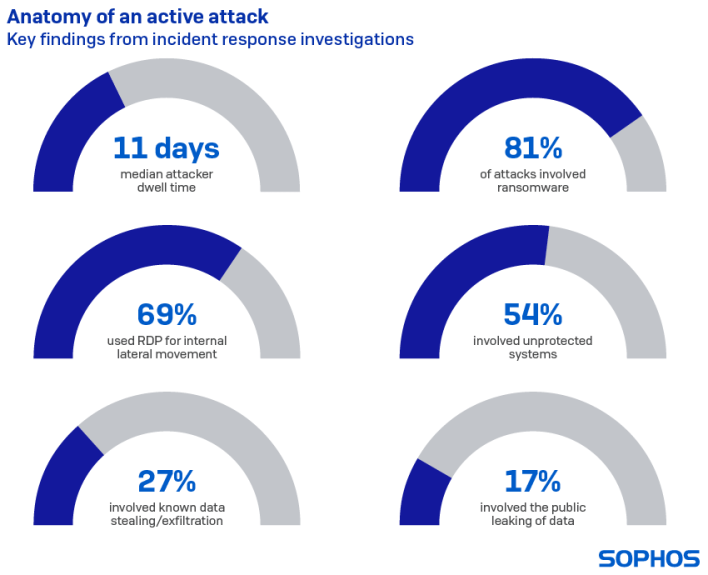
After a cybercriminal manages to breach a network, it is not all about immediately attacking the target. New research shows that these black hat hackers may lie dormant or lurk on a network for around 250 hours on average before an attack kicks off or they are detected. This means that organizations should know that the clock is always ticking to quarantine a problem before it turns into a nightmare, like the recent Colonial Pipeline attack.
Defending an organization from cyberattacks is no small feat when the threat constantly adapts to new evasion techniques and evolves the attack toolset. Generally, these adversaries like to try and stay one step ahead of the security team and often are; however, the tables can turn when companies invest in solving the problem adequately. Moreover, when research like what is done by cybersecurity company Sophos is published, more people know what to look for, thus making companies safer.
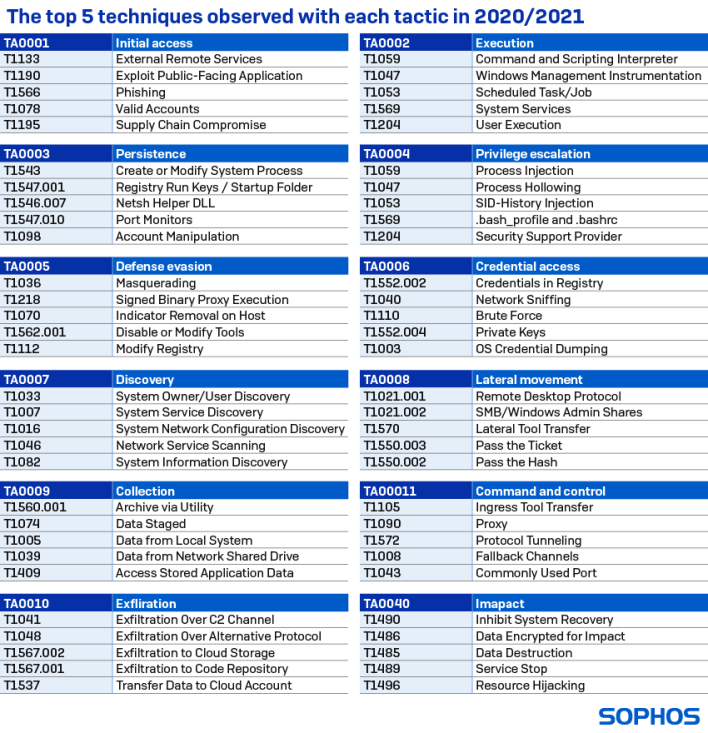
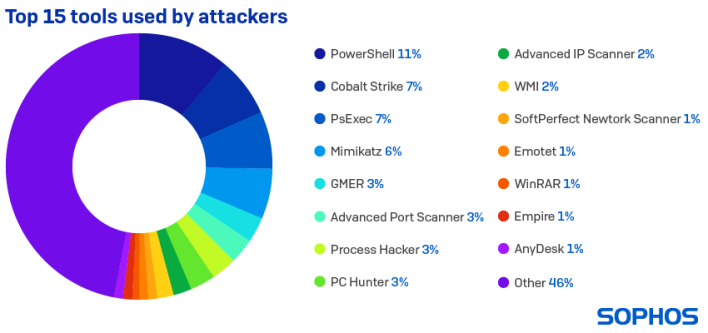
Similarly, there are also correlations between the tools hackers use, such as when “PowerShell is used in an attack, Cobalt Strike is seen in 58% of cases, PsExec in 49%, Mimikatz in 33%, and GMER in 19%.” This can serve as an early warning system for “impending attack or confirm the presence of an active attack.”
With this abundance of information in mind, all organizations are always a target, and each needs to be aware that a cybersecurity threat could appear at any time. Using Sophos’ research, though, security teams will hopefully be better equipped to tackle threats as they come up in the future. As it goes, it is not a matter of if, but when you are breached.

