Steam, Epic, GOG Accounts Targeted By Ruthless BloodyStealer Trojan

Do you still think of video games as kids' stuff? A surprising number of people are still of the mindset that video games are small-time, but the reality is that last year, per IDC data, video games drew more revenue ($179 billion) than both films and professional sports combined ($175 billion). That's a lot of money changing hands, and much of that money is spent adding digital licenses to accounts with services like Steam, Xbox, PlayStation, and so on.
Knowing that, it becomes obvious that these accounts are like candied sweets for online predators. We're not talking about the "why don't you have a seat" type of online predators—instead, we're talking about folks who deploy phishing and malware tools to capture the accounts of innocent gamers that fall prey to their tricks. Such accounts can be worth hundreds or thousands of dollars, so even if they usually sell for a fraction of their value, they can still be quite lucrative.
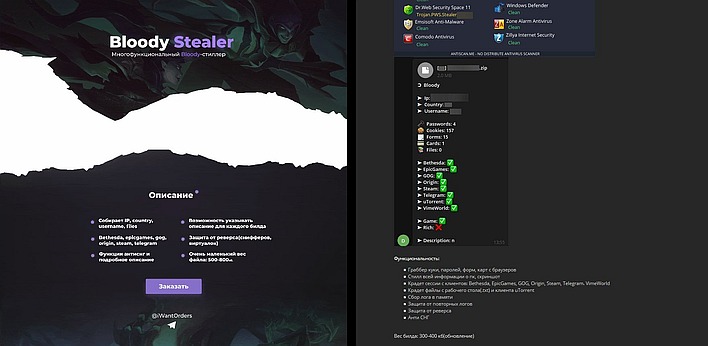
Kaspersky notes that BloodyStealer has already circumnavigated the globe despite being a relatively new piece of software. It's notable not only for its rapid spread, but also for its advanced capabilities. The security firm says that the trojan has a whole suite of tools meant to thwart security analysis, and that the stolen information is sent to a private command-and-control server that is protected against DDoS attacks. From there, it can be accessed using a bespoke control panel or via Telegram.
Naturally, the company recommends its own software, Kaspersky Security Cloud, to protect gamers from Bloodystealer. However, Kaspersky also offers some general tips to avoid being victimized by this and other, similar malware: use strong passwords, use two-factor authentication, stick to official sources for software downloads, be wary of links from strangers, and make sure any site you're slapping your credentials into is the real deal. All quite standard advice, but it's almost depressing how often people slip up on these simple ideas.

