SweynTooth Bluetooth LE Security Flaw Threatens Thousands Of Devices From Samsung, FitBit And More

But with that ease of use and convenience comes some security pitfalls according to a research team from Singapore. Researchers from the Singapore University of Technology and Design have outlined a collection of 12 Bluetooth Low Energy (BLE) exploits that it has dubbed SweynTooth.
More specifically, SweynTooth affects the software development kits (SDKs) that underly and enable BLE communication. Various vendors manufacturer BLE chips that are then sold to companies that implement them into their products. BLE is mainly found in IoT devices and smart devices that need to keep a very low power profile in order to preserve battery life.
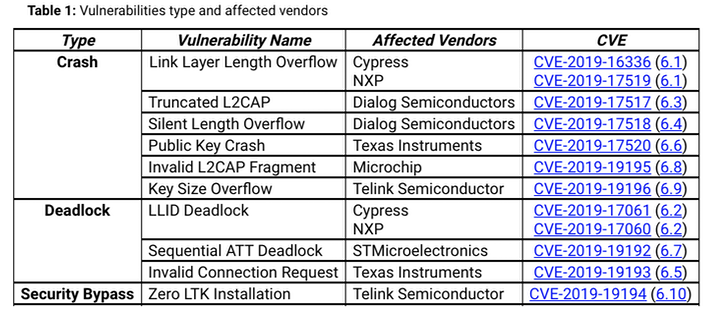
"At first glance, most of the vulnerabilities affect product’s availability by allowing them to be remotely restarted [crash], deadlocked or having their security bypassed," writes the researchers. With regards to crashes, a device can be remotely triggered to experience a hard fault (i.e. memory corruption) that would cause a device to restart. Deadlocking occurs due to a hard fault that can interrupt the function of device.
"Crashes originated from hard faults, if not properly handled, can become a deadlock if the device is not automatically restarted," the report adds. "In most cases, when a deadlock occurs, the user is required to manually power off and power on the device to re-establish proper BLE communication."
With the security bypass, an attacker has the ability to gain read/write access to the device, which the team considers the most critical vulnerability.
In their testing, the three researchers discovered SweynTooth vulnerabilities in BLE SoCs from the following vendors: Texas Instruments, NXP, Cypress, Dialog Semiconductors, Microchip, STMicroelectronics, and Telink Semiconductor. According to the team, it reached out to all of the named companies, and most have released patches that are meant to stop the SweynTooth threat. However, those patches are useless if they don't make their way to the actual products that incorporate the BLE chips used by customers.
This might be relatively simply for a device like an Amazon Echo that receives constant, automatic updates. However, this might be more problematic for other smart home sensors or smart plugs, for example, which customers usually setup once and then let them perform the intended tasks unhindered.
Vulnerable devices include the Fitbit Inspire smartwatch line, Eve Smart Home systems, Samsung Galaxy Fit, and August Smart Lock (among others). In the case of the Fitbit Inspire, SweynTooth allowed buffer overflows, which would then cause the device to restart. With the August Smart Lock, a Silent Length Overflow vulnerability was verified, which could allow a hacker to gain access control over the device.
But that's nothing compared to vulnerabilities with medical devices. "The most critical devices that could be severely impacted by SweynTooth are the medical products. VivaCheck Laboratories, which manufacture Blood Glucose Meters, has many products listed to use DA14580," the team writes. "Hence all these products are potentially vulnerable to the Truncated L2CAP attack. Even worse, Syqe Medical Ltd. and their programmable drug delivery inhalation platform (Syqe Inhaler v01) is affected alongside the latest pacemaker related products from Medtronic Inc."
If there's any consolation to the SweynTooth racket, it's that attackers have be in very close proximity to their intended victim (due to the signal limits of BLE). To learn more about SweynTooth, be sure to check out this website dedicated to the BLE vulnerabilities.

