How Tech-Savvy Thieves Are Stealing Cars By Hacking Through Headlights

If you notice your car's side panels have been tampered with or error messages from your car, there is a chance that thieves are taking a crack at stealing the vehicle. This happened to Ian Tabor in April of 2022 after finding his front bumper and trim pulled off with headlight wiring undone. Then, the same thing happened again just three months later, followed by a full theft of the vehicle a few days after the second tampering. It had looked like the headlights were the access point for the theft, but how could this have happened?
As Dr. Ken Tindell, CTO of Canis Automotive Labs, outlines in his blog post, most cars have "sophisticated car security systems, including an engine immobilizer," so this must have been bypassed to steal the car. The first clue into unraveling what happened lies with the 'MyT' telematics system that Toyota ships with its vehicles. Long story short, MyT is a diagnostic system that sends "Diagnostic Trouble Codes" or DTCs to Toyota servers and the owner of the vehicle through the MyT app. This system can show problems in different systems through faults detected and reported by an Electronic Control Unit (ECU), which, in modern vehicles, can be networked with other ECUs or other systems in a vehicle through the Controller Area Network (CAN) bus.
It is also noted that ECUs can detect faults by noting an inability to communicate with other ECUs in the vehicle based on the timing of messages sent. With this, many DTCs were detected in Ian's RAV4 that was stolen, and the common denominator here was the CAN bus.
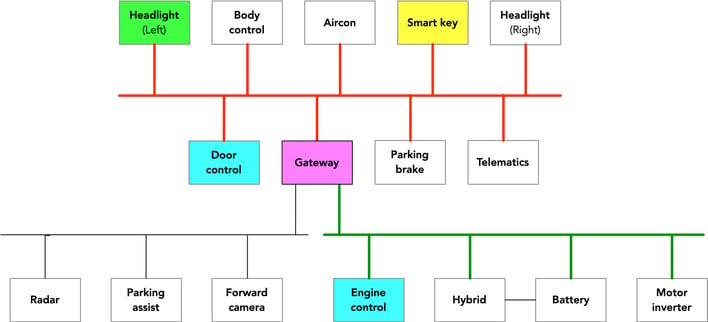
While the CAN bus is not new technology, it is not perfect either and it shows due to issues such as those discovered by Dr. Tindell. Effectively, the thieves break into the car's communications in the CAN bus and insert fake messages spoofing the smart key receiver on the same network as the headlights, diagrammed above. These messages, which can unlock the engine immobilizer and doors, are then passed from the originating network to the network with engine control and other features.

While it sounds complex, this attack can be done with a modified USB cable and JBL Bluetooth speaker, or at least its shell. Within this fake speaker is about $10 in components attached to the JBL board in the speaker housing, so it doesn't look like a thief has car-stealing equipment.
You can see what this looks like externally in the video above, and it is unsettling thanks to the knowledge that communications over the CAN bus are not very secure. Considering this and the fact that CAN bus technology is used in cars, planes, boats, tractors, and more, it can be positively terrifying. However, thankfully, manufacturers are working to secure CAN bus communications, but the real question is, what will come next?
(Images courtesy of Ian Tabor and Ken Tindell)

