This Novel Raspberry Pi Project Uses Electromagnetic Waves To Detect Hard To Find Malware

The Raspberry Pi is terrific for plenty of uses, from retro-style gaming to running an extremely low-cost server. A team of researchers have discovered another new use for Raspberry Pi: hands-off malware detection.
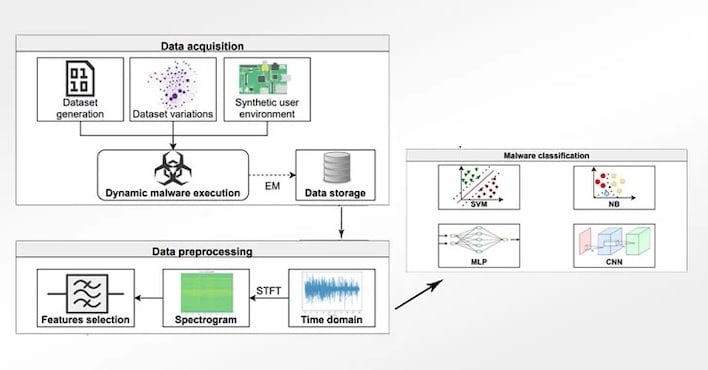
While most virus and malware detection depends on file signatures and behaviors, this new project scans for specific electromagnetic (EM) waves. This is especially important for picking up on infections with Internet of Things (IoT) devices, which often can’t run traditional antivirus software.
At the Research Institute of Computer Science and Random Systems (IRISA) in France, four team members from Université de Rennes published the current results of their project. The team also presented its findings to the Association for Computing Machinery’s Annual Computer Security Applications Conference (ACSAC) in December 2021. Duy Phuc Pham, Damien Marion, Matthieu Mastio, and Annelie Heuser presented "a novel approach of using side channel information to identify the kinds of threats that are targeting the device."
The Raspberry Pi, since it’s focusing on the EM field surrounding a potentially-infected device, operates without being connected to or installing any software on the target. It features on oscilloscope, specifically the Picoscope 6407, and an H-Field probe to pick up on changes to the EM field.
The authors recorded 100,000 measurement traces from an IoT device infected by samples of different in-the-wild malware, along with activity on the devices that might be out of the ordinary but still completely harmless.
Using Convolution Neural Networks to evaluate threats, they built a model that provided accuracy as high as 99.82 percent during testing. They were able to predict three generic types of malware, along with one benign class of unwanted software.
Even better, the Raspberry Pi-based detection system could “see” through common types of malware obfuscation. It didn’t matter what steps the malware took to hide itself on the affected system, the IRISA team’s detection algorithm was able to recognize the infection based on changes in the EM field.

