Better Scan Your PC For Malware If You Installed This Super Mario Game

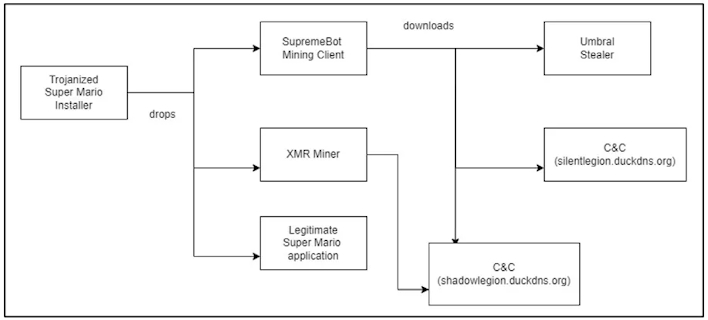
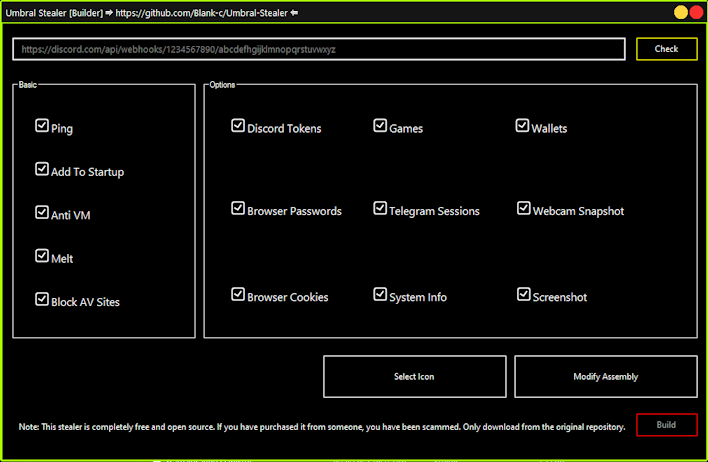
While the legitimate Super Mario game is running normally, a Monero miner and SupremeBot mining client are installed in the background to kick off the infection chain. The mining client then establishes communication with a command and control (C2) server to pull the miner configuration to the victim’s machine. Further, the client also downloads the open-source Umbral Stealer information-stealing malware, which takes sensitive data from browsers, captures screenshots and webcam images, goes after cryptocurrency wallets, and more. This information is then shipped off via Discord webhook to the threat actor’s server on Discord.
Of course, this is not the first time a threat actor has used games as a disguise for malware, such as the recent Pokémon NFT card game malware or the earlier Epic Games launcher malware. Given this and older incidents, it is always good to ensure you are getting a game installer from the source and not a third-party location. Moreover, turning your antivirus or other security solution on and verifying it is up to date would be worthwhile, even if that is simply Microsoft Defender. You never know what could be lurking in any installer.

