How Hackers Using Old Tricks Are Gaming News Media To Brazenly Distribute Malware

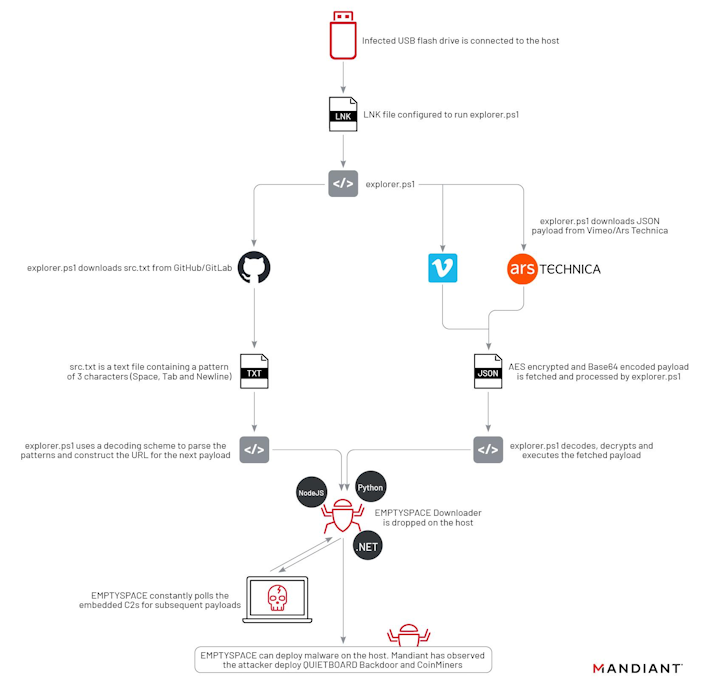
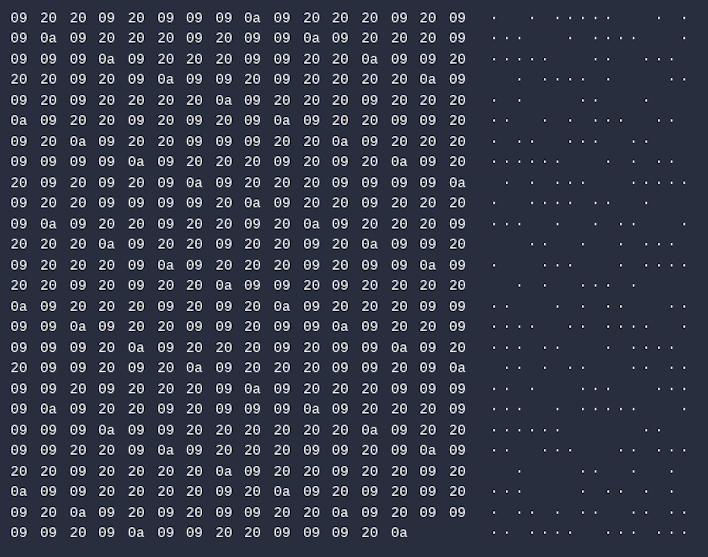
If you were to be breached by UNC4990, the first stage of compromise begins with a USB drive containing a malicious LNK shortcut file. Once clicked, this file, which might be labeled with the brand and size of the USB device, executes a PowerShell script called explorer.ps1. This script has a variety of versions and iterations, but this is not necessarily the interesting part. Originally, this script fetched a script from a malicious URL hardcoded in the script, which was updated to point at a GitHub repository containing a text document with tabs, spaces, and line feed characters. When viewing this, it would appear blank, but each of those characters could be converted to binary, which could be converted to another URL where a final executable file could be downloaded.
As of 2023, though, all these methods of getting later stages of malware have been replaced with the use of public-facing services to host encrypted malicious content. At first, UNC4990 used Vimeo and information inserted into the description of a Pink Floyd video, which has since been removed. Once this video was removed, Mandiant researchers found that the group switched over to using data stored in the “About” section of an Ars Technica user.
Regardless of the methods to pull it, all these stages resulted in the download of malicious software dubbed EMPTYSPACE, a “downloader that communicates with its C2 server over HTTP.” This software would then pull an executable payload from the command and control (C2) server, which may be a backdoor or a cryptocurrency miner, depending on the target.
At the end of the day, this malware chain could have been prevented by people who knew not to plug in random USB drives or randomly click around on files they were unsure of. Ultimately, the field of cybersecurity is a team effort that everyone has a stake in. So next time those mandatory trainings come around, heed their warnings because the oldest tricks in the book are still working but with new twists.