Gaping Security Hole In Windows 11 And 10 Could Give Hackers Full Control Of Your PC
Microsoft is warning of a vulnerability in both Windows 11 (not yet released, but available in preview form to Windows Insiders) and Windows 10 that could reveal a user's admin password, which in turn could be used to elevate their own system privileges. That's obviously not a good thing, as it would essentially grant the hacker with full control of a system.
"An elevation of privilege vulnerability exists because of overly permissive Access Control Lists (ACLs) on multiple system files, including the Security Accounts Manager (SAM) database. An attacker who successfully exploited this vulnerability could run arbitrary code with SYSTEM privileges. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights," Microsoft explains.
This is the latest in a string of security holes that have come to light in recent weeks. First it was the PrintNightmare fiasco, which described a vulnerability within the Windows Print Spooler service. If leveraged, a hacker could remotely execute code on a victim's PC. Adding insult to injury, a mandatory patch for the flaw caused some printers to stop working.
Then another Windows Print Spooler bug crawled into view, though at least in that case, an attacker would need physical access to a PC in order to exploit it. Microsoft also recently rolled out a patch for a Windows Hello vulnerability that could otherwise allow an attacker to bypass facial recognition on a Windows PC (with a little work).
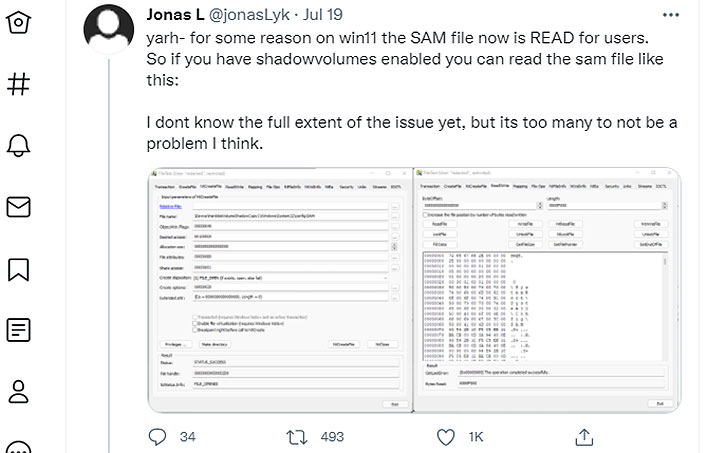
This latest one has two names—HiveNightmare and SeriousSAM. Security researcher Jonas Lykkegaard noted the flaw on Twitter after discovering that the Security Account Manager database file was able to be read by all users.
"Yarh—for some reason on Win11 the SAM file now is READ for users.
So if you have shadowvolumes enabled you can read the SAM file like this:
I don't know the full extent of the issue yet, but its too many to not be a problem I think," Lykkegaard stated.
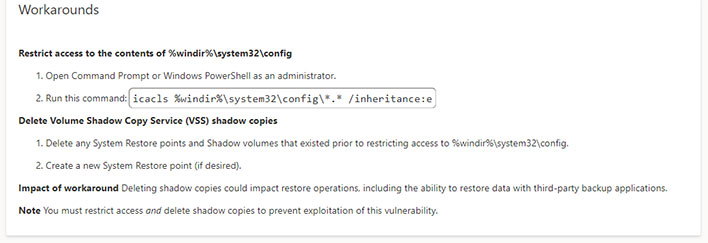
While there is no patch available yet, Microsoft did at least offer up a workaround for SeriousSAM/HiveNightmare, outlined in CVE-2021-36934. Here it is...
What's at stake here is that a user with limited privileges could gain access to a system's admin password, then elevate their own privileges. From there, they could wreak all kinds of havoc, from reading and deleting important files, to installing malware, and so forth. According to Microsoft, this affects Windows 10 version 1809 and newer operating systems.
Hopefully this will be patched up soon. In the meantime, give the above workaround a shot if you're worried about this one.