US Federal Agencies Uncover Massive Chinese Hacker Cyber Espionage Spying Campaign

Much of the discussion surrounding cyberwarfare has centered around Russia and Ukraine, in recent months. While it may have been pushed into the background, however, China’s aggressive cyber activity continues apace, whether it rises to the level of warfare or not. Only a month ago, we covered news that Chinese state-sponsored hackers had been deploying malware to steal US intellectual property in an operation that went undetected for years. Just a month before that, we wrote about a Chinese state-sponsored hacking group that had been using VLC Media Player to deploy malware in targeted attacks on foreign governments and NGOs.
Both of these Chinese-backed cyber operations were discovered by private cybersecurity researchers, but US federal agencies have been monitoring Chinese cyber activity as well. This week, the National Security Agency (NSA), Cybersecurity & Infrastructure Security Agency (CISA), and Federal Bureau of Investigation (FBI) published a joint cybersecurity advisory detailing ways that Chinese state-sponsored hackers have been compromising network providers and devices in order to snoop on network activity and steal credentials.
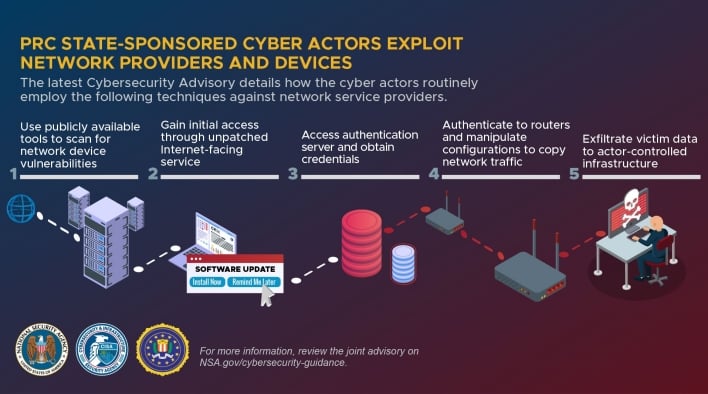
According to the advisory, this cyber espionage is widespread and doesn’t solely target large network infrastructure, but also smaller, commercial network devices, like routers and Network Attached Storage (NAS) devices. The Chinese hackers carry out this activity by exploiting known vulnerabilities in network devices. In many cases, the vendors who manufacture these network devices have released patches that fix the vulnerabilities, but network administrators have neglected to update the devices. The following table lists the known network devices vulnerabilities most commonly leveraged by Chinese-backed hackers.
| Vendor | CVE Identifier |
Vulnerability Type |
Severity |
| Cisco | CVE-2019-11510 | Remote Code Execution |
9.8 Critical |
| CVE-2019-15271 | Remote Code Execution | 8.8 High |
|
| CVE-2019-1652 | Remote Code Execution | 7.2 High |
|
| Citrix | CVE-2019-19781 | Remote Code Execution | 9.8 Critical |
| DrayTek | CVE-2020-8515 | Remote Code Execution | 9.8 Critical |
| D-Link | CVE-2019-16920 | Remote Code Execution | 9.8 Critical |
| Fortinet | CVE-2018-13382 | Authentication Bypass |
7.5 High |
| MikroTik | CVE-2018-14847 | Authentication Bypass | 9.1 Critical |
| Netgear | CVE-2017-6862 | Remote Code Execution |
9.8 Critical |
| Pulse | CVE-2019-11510 | Authentication Bypass |
10 Critical |
| CVE-2021-22893 | Remote Code Execution |
10 Critical |
|
| QNAP |
CVE-2019-7192 | Privilege Elevation |
9.8 Critical |
| CVE-2019-7193 | Remote Inject |
9.8 Critical |
|
| CVE-2019-7194 | XML Routing Detour Attack |
9.8 Critical |
|
| CVE-2019-7195 | XML Routing Detour Attack |
9.8 Critical |
|
| Zyxel | CVE-2020-29583 | Authentication Bypass |
9.8 Critical |
Just two days after US federal agencies published this cybersecurity advisory, independent cybersecurity researchers at Sentinel Labs published details on Aoqin Dragon, a Chinese state-sponsored hacking group. According to the researchers, these hackers have been conducting cyber espionage against Singapore, Hong Kong, Vietnam, Cambodia, and Australia. The researchers traced this activity all the way back to 2013, when Aoqin Dragon used malicious Microsoft Word documents to install backdoors in target systems.
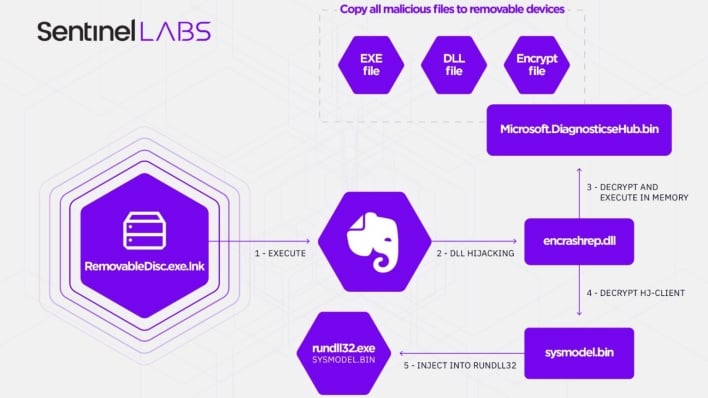
The Chinese hacking group’s tactics have been through multiple changes since 2013. Around 2016, the group moved from malicious Microsoft Word documents to fake antivirus executables. Then, in 2018, Aoqin Dragon shifted to using fake removable devices and is still using that strategy at present. The group uses “RemovableDisc” shortcuts that launch “RemovableDisc.exe.” This executable installs malware that runs on device startup as “Evernote Tray Application.” This malware installs two additional malware payloads. The first payload copies the malware to all removable devices, and the second payload installs a backdoor that communicates with the hackers’ command-and-control (C2) infrastructure.

