How Security Evading Virtualized Malware Abuses Google Ads And Infects PCs

Last year saw a rise in threat actors abusing Microsoft Office macros to infect their victims’ systems with malware, prompting Microsoft to block macros embedded in documents downloaded from the internet. In response, threat actors have had to pivot to alternative malware distribution and infection methods, including malvertising. Malvertising involves placing ads that either directly distribute malware or trick users into downloading it. New research by the cybersecurity firm SentinelLabs shows that, lately, malware distributed in this manner employs virtualization to hide its malicious nature from anti-virus scanners.
Researchers at SentinelLabs have recently observed a family of malware loaders that make use of KoiVM .NET virtualization, which obfuscates code by replacing it with virtualized code that is understood only by the virtualization framework. When the malware loaders are launched, a virtual machine engine translates the obfuscated code into the original code. Thus, the malicious code is obscured until it is already running, at which point it’s too late for anti-virus software to preemptively detect the presence of malware and warn the user.
Researchers at SentinelLabs have recently observed a family of malware loaders that make use of KoiVM .NET virtualization, which obfuscates code by replacing it with virtualized code that is understood only by the virtualization framework. When the malware loaders are launched, a virtual machine engine translates the obfuscated code into the original code. Thus, the malicious code is obscured until it is already running, at which point it’s too late for anti-virus software to preemptively detect the presence of malware and warn the user.
The researchers have dubbed these kinds of malware loaders “MalVirt.” Many of these also loaders leverage additional obfuscation techniques, including malicious string encryption and decoy command-and-control (C2) servers. SentinelLabs is currently tracking an on-going MalVirt campaign distributing infostealer malware, namely Formbook and XLoader. This sort of malware exfiltrates passwords and other sensitive information from infected systems.
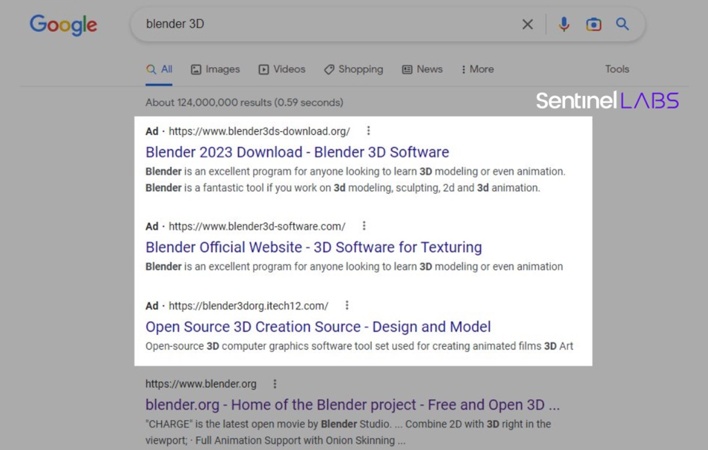
This campaign abuses Google Ads to place links to malicious websites at the top of the Google Search results. These websites mimic those of legitimate software, bearing similar domain names and often appearing almost visually identically. However, when users attempt to download the advertised software from these websites, the websites serve up MalVirt loaders instead. In order to avoid accidentally downloading malware from one of these sites, it may be best practice for users to avoid clicking on search results with the “Ad” label altogether.
This campaign abuses Google Ads to place links to malicious websites at the top of the Google Search results. These websites mimic those of legitimate software, bearing similar domain names and often appearing almost visually identically. However, when users attempt to download the advertised software from these websites, the websites serve up MalVirt loaders instead. In order to avoid accidentally downloading malware from one of these sites, it may be best practice for users to avoid clicking on search results with the “Ad” label altogether.

