Microsoft Flags Windows 10 Hosts File Telemetry Data Blocking As Security Threat

Hosts is a text file that is located at C:\Windows\system32\driver\etc\HOSTS and is used to map connections between an IP address and a domain name. Putting addresses in a hosts file typically allows your computer to resolve the address faster than going through your dynamic name server (DNS).
You can also use the hosts file to block your computer from reaching out to certain websites. For example, if a parent wanted to discretely block Facebook on their child's computer, they could enter in the following text string in the hosts files:
127.0.0.1 www.facebook.com
And this is where Microsoft's recent actions come into play. Many Windows 10 users aren't too happy about telemetry data that the company collects automatically. So, they have been manually entering certain Microsoft domains into the hosts file with the 127.0.0.1 prefix to prevent telemetry data from being sent back to the mothership.
- telemetry.microsoft.com
- watson.live.com
- watson.microsoft.com
- telemetry.remoteapp.windowsazure.com
- telemetry.urs.microsoft.com
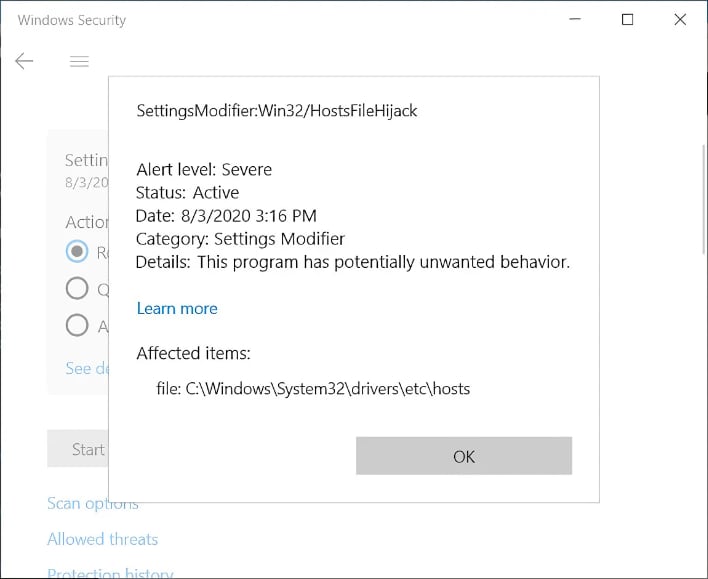
Windows Defender now flags any edits made to the hosts file that include specific Microsoft domains, and labels it as a “SettingsModifier:Win32/HostsFileHijack” threat according to Bleeping Computer. If you decide to remove this “threat”, your hosts file is reverted back to its default state. Microsoft describes this threat, writing:
The Hosts file is used by your web browser to find out where to redirect certain IP address calls. Malicious or unwanted software can modify this file to prevent users and applications from accessing certain websites. Or the malware may force you to visit other websites instead.
And for anyone that attempts to modify and save the hosts file with one of the affected Microsoft servers after the fact will see the following message: "Operation did not complete successful because the file contains a virus or potentially unwanted software". Now there is no question that certain malware can strike your hosts file, make modifications, and make your system vulnerable to threats. However, the modifications to block certain Microsoft servers made by discerning Windows 10 users seems harmless at face value. In essence it's Microsoft's way of slapping you on the wrist for "Taking sides against the family".

Microsoft’s solution to sidestep the issue if you have personally modified your hosts file is to put it on the exclusions list with your antivirus program. However, that keeps you unprotected if malware does attempt to modify it at a later date. So, if you’re paranoid about Microsoft collecting data on you, maybe your best course would be to tread lightly.

