Windows Hello Biometric Security Has Been Compromised With An Elaborate Spoof

Over the past few years, biometric security solutions have been on the rise, replacing the use of traditional passwords on both mobile devices and the PC. Windows Hello is one such implementation. It allows users to near-instantaneously log onto their machines with their face or fingerprint (or a PIN), and is in wide use today. It's also apparently vulnerable to an exploit that could allow an attacker to bypass facial recognition on a Windows PC.
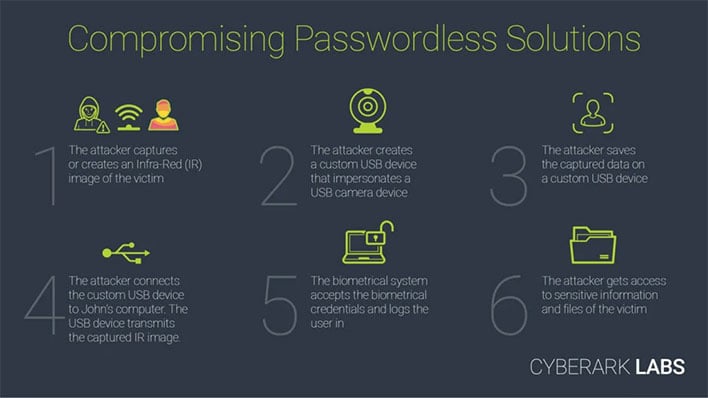
Any vulnerability is concerning because of Windows Hello's massive footprint—Microsoft's telemetry suggests the vast majority of Windows 10 users (85 percent) use Windows Hello. Because it is so widely used, security researchers at CyberArk Labs went on the hunt for potential attack vectors related to Windows Hello, and found what they say is a "design flaw," that involves spoofing the victim.
This vulnerability is tracked as CVE-2021-34466. Fortunately, there is no evidence to suggest that anyone is actually leveraging this potential attack vector in the wild, but the potential is still there. This is probably not something the average user needs to worry about, though anyone in possession of sensitive data—journalists, scientists, people in the financial industry, and so forth—could be attractive targets to someone who is motivated.
It is a fairly simple and quick attack, once it is configured. All a malicious actor has to do is plug in the USB device containing an infrared frame of the victim into their PC, and when the login screen comes up, just click the facial recognition button to thwart Windows Hello.
The full Windows Hello vulnerability report gets into the fine grain technical details of the hack, but the general takeaway is that this is something that should be patched. And fortunately, Microsoft has issued security updates for various versions of Windows, to address the exploit.
One thing worth noting is that according to Microsoft, users with Windows Hello Enhanced Sign-in Security are immune this attack vector. But whether you fall into that category or not requires a bit of research.
"Enhanced Sign-in Security is a new security feature in Windows which requires specialized hardware, drivers, and firmware that are pre-installed on the system by device manufacturers in the factory. Please contact your device manufacturers for the state of Enhanced Sign-in Security on your device," Microsoft said in a statement.
If you think you are affected or just want to play it safe, head over to the CVE-2021-34466 landing page and download the security update whatever version of Windows you are running.