Alarming WordPress Plugin Security Flaw Leaves 2M Sites Vulnerable To Attack

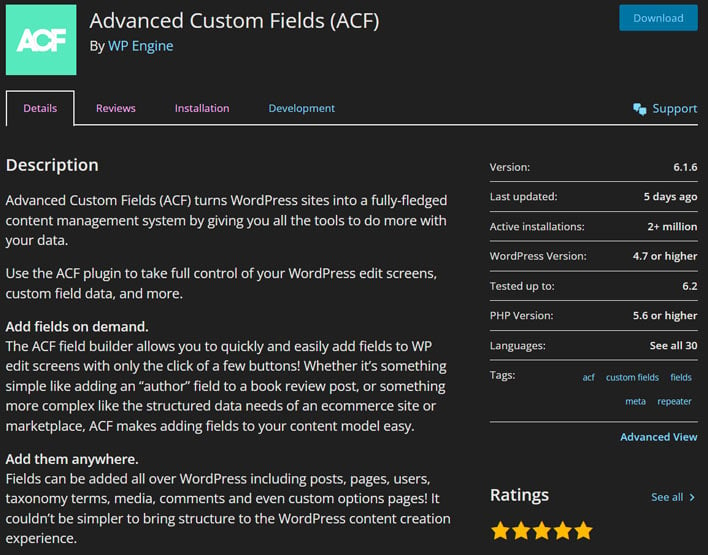
Before we go on, it is important to note that the Advanced Custom Fields plugin has been patched, with the release of version 6.1.6, and that is why security researchers can now talk openly about the headlining flaw.
The ACF plugin's reflected XSS vulnerability would allow unauthorized users of the site to potentially steal sensitive information. It was possible that a malicious actor could use the plugin's vulnerability to inject malicious scripts, such as redirects, advertisements, and other HTML payloads. Later, when guests visited the site that had been tampered with, the malicious scripts could execute.
Exploiting the plugin flaw in the plugin isn't a trivial task, though. In order to do their dirty deeds, a malicious actor needs to prepare, and indulge in some subterfuge. The reflected XSS vulnerability requires a would-be attacker to trick a privileged user into visiting a crafted URL path on the site. Only subsequently, after gaining escalated privileges, are they be able to start injecting code due to the vulnerability in ACF versions prior to 6.1.6.
WordPress is one of the most popular content management systems (CMS) available, accounting for over 40% of the content on the web, and is therefore a big target for hackers. In addition to the core CMS code, WordPress installs are usually stuffed full of custom code in the form of themes, extensions and plugins. All of these components - and the hosting server - expose a very broad attack surface for hackers and malicious actors.
The developers of WordPress and security plugins have done a lot over recent years to shut down vulnerabilities with auto-updates and more, but the openness of the system, number of plugins, people neglecting their online properties, and more can mean owning a WordPress site is like running a digital whack-a-mole machine.