WordPress Plugin Exposes 11M Sites As Hackers Exploit An Alarming Security Flaw
Elementor is a Squarespace-like website builder to go over the top of WordPress, allowing drag-and-drop customization of a site without having to know programming or design. However, in versions before 3.11.7 with the premium edition of the tool, website owners who also used WooCommerce were vulnerable to full site takeover.
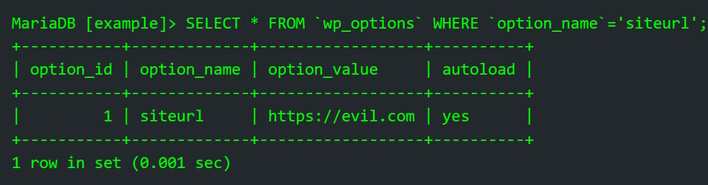
This vulnerability is thanks to a string of features outlined in a blog post from Ninja Technologies Network, which explains that an Elementor site with WooCommerce loads “elementor-pro/modules/woocommerce/module.php.” This component registers an AJAX action called “pro_woocommerce_update_page_option,” which would allow an Administrator or Shop Manager to update WooCommerce options within the database containing configurations and options. However, the function that is called behind the “pro_woocommerce_update_page_option” does not have user input or privilege validations, meaning that any user of any privilege level can modify options.
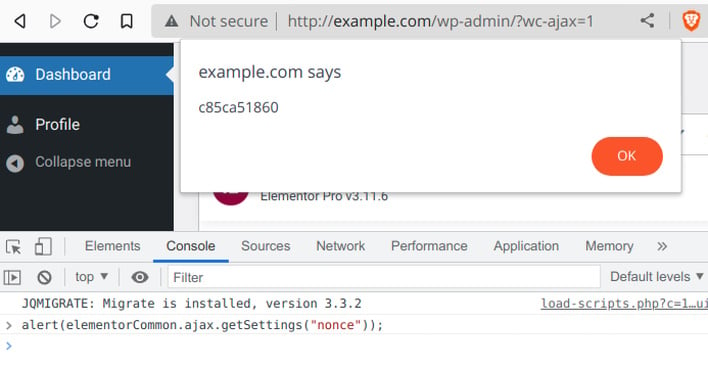
While there are some protections upstream of this function that could prevent this attack from happening, it is possible to leak sensitive information to bypass these protections with any logged-in user account. With this all in mind, an attacker could create an administrator account, redirect site traffic to a malicious site, or do other nefarious activities.
Thankfully, this vulnerability has since been patched on March 22nd, just four days after it was discovered and reported to the authors. However, Patchstack reports seeing active exploitation from several IP addresses, files being uploaded to vulnerable sites, and site URLs changing to attacker-controlled locations. Thus, those who use a premium version of Elementor and WooCommerce should update their sites to Elementor version 3.11.7 or later.

