XCSSET macOS Malware Caught Stealing Screenshots And Exploiting 0-Day Bugs, Update Now

It is time to update macOS devices as a new 0-day has been found that allows malware to bypass privacy protections. The logic bug allowed any app to inherit another app’s permissions to take screenshots or do other activities without the end-user knowing, making this quite concerning.
In 2020, malware called XCSSET made an appearance using two 0-day exploits to target Xcode developers and their projects. It would primarily spread using these projects, some of which were shared on GitHub, “leading to a supply-chain-like attack for users who rely on these repositories as dependencies in their own projects,” as researchers at Trend Micro explain. Since the initial discovery, the malware has had an ebb and flow, making a resurgence earlier this year by stealing cryptocurrency on Apple M1 systems.
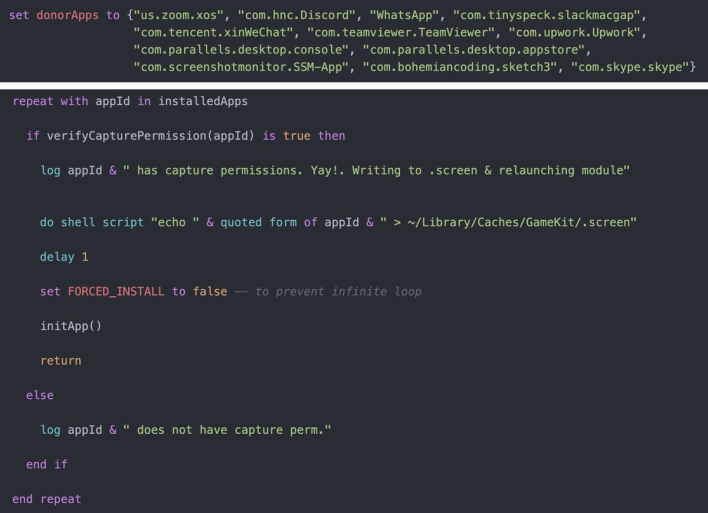
Most recently, Apple patched a new 0-day vulnerability in macOS 11.4 (CVE-2021-30713), which could have allowed bypass of the Transparency Consent and Control (TCC) framework that controls what hardware and software an application has access to. To exploit this, an attacker could hide within another application that has regularly granted permissions that it is looking for. The sub-application would then inherit the parent or donor application’s permissions, which is quite a privacy concern.
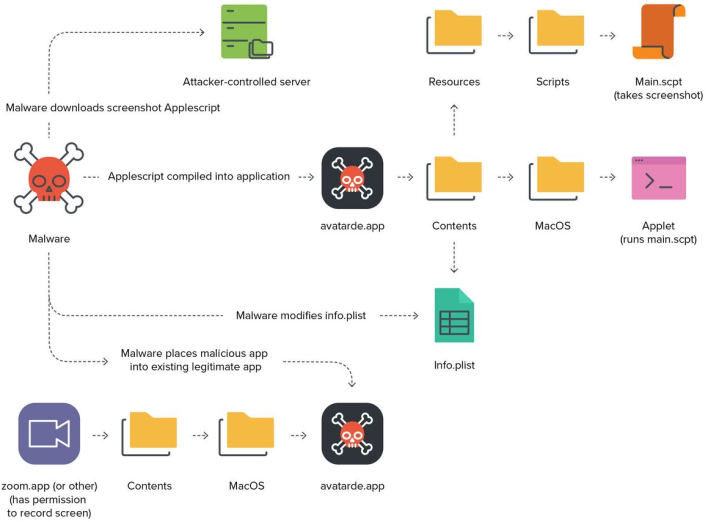
Thankfully, this issue has now been fixed in macOS 11.4, as mentioned, so it is time for all users to update their systems to the latest macOS update. However, XCSSET primarily targeted developers using Xcode, so it is unlikely for the average person to be affected. If you are still concerned about this, though, you can check to see if you were comprised using the indicators Jamf lists in its blog post.

