Apple Accused Of Ignoring Three 0-Day Vulnerabilities And Skirting Bug Bounties
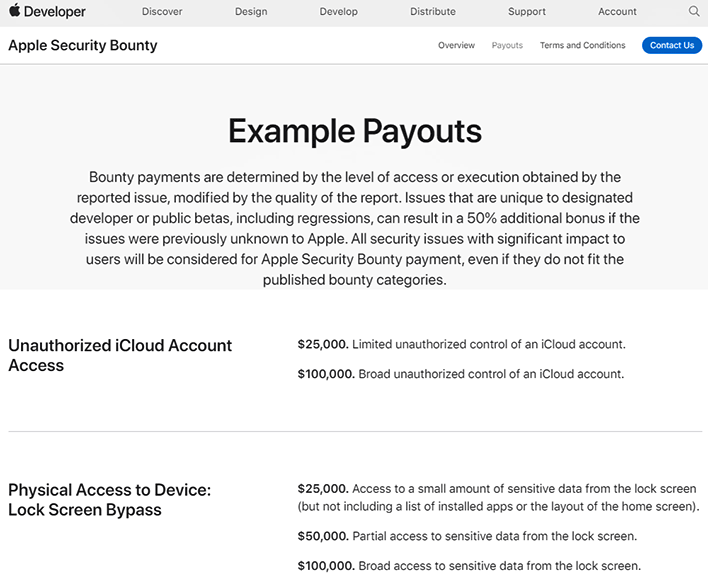
In a recent Washington Post article, several security researchers shared their own frustrating stories of dealing with Apple's bounty program. The complaints ranged from ignored submissions to unpaid bounties for vulnerabilities that did ultimately get fixed. This is obviously a bad look for Apple, a company that famously claims to have its users' security and privacy at heart and then stabs itself in the back with bad plans like scanning all iCloud photos or trying to automatically diagnose mental health disorders.
Following the article, other security researchers have come forward with their own series of complaints. Like the article, accusations range from ignoring submissions to just flat-out not paying for the work that went into the bugs Apple has fixed. The most credible of these accusations from a researcher named Denis Tokarev, who posted under the screen name illusionofchaos. In a detailed blog post, Tokarev goes into great detail about zero-day vulnerabilities in three Apple services first reported as early as April of 2021, most of which still go unpatched in the recently-released iOS 15 today.
Up first is a doozy: Apple seems to have been including medical and screen time data in calls to the com.apple.analyticsd XPC service. The service's log-dump command would provide what can only be described as entirely too much information to any app that asked for it. This was apparently fixed in iOS 14.7 released in late July, but Tokarev claims in the blog post that he first reported it on April 29. Apple seemingly ignored his requests and never made mention of the issue in the security notes for any iOS update since then. It seems that Apple is just not going to pay Tokarev for his discovery.
Lastly, two different vulnerabilities exist in the com.apple.nehelper XPC service but it's unclear if they're really security threats. One seems relatively minor, in which any app can access a method that takes an app bundle ID and returns data about whether the app is installed. iOS apps are supposed to interact with other apps via the other app's URL scheme, but in all reality this seems relatively minor. More glaring is that com.apple.nehelper accepts an app-provided string to see which version of the iOS SDK was used to build it, rather than looking at the manifest. That would potentially give the ability to skip entitlement checks, ultimately grabbing Wi-Fi network information that it shouldn't. It's unclear whether the network WPA2 key is included in the returned data, so it's possible that it doesn't ultimately open the user to issues, but again, it seems like a trivial fix.
Tokarev did update his post this morning to say that Apple did finally respond. The company told him that it is "still investigating these issues and how we can address them to protect customers." Considering how many researchers have run into similar roadblocks of late, it seems that Apple either has its hands full with iOS being full of holes or is just dragging its feet on paying the bounties it promised.

