iOS Devs Warn Apple Apps Ignore Privacy Settings And Track A Shocking Amount Of Data

Two iOS developers used a jailbroken iPhone to decrypt and analyze network traffic between the device and Apple. What the developers found is that many of Apple’s own apps frequently send detailed user behavior data along with unique device identifiers back to Apple even when analytics sharing, personalized ads, and personalized recommendations are all disabled. This data collection appears to conflict with Apple’s stated mission of protecting user privacy.
Nonetheless, these new findings aren’t super surprising. In December 2020, Apple implemented its App Tracking Transparency (ATT) feature, which shines light on the data collection and sharing practices of apps in the App Store and gives users the option of disabling tracking and data sharing when it involves third-parties. However, while ATT can block apps from tracking users across third-party apps and websites, first-party in-app tracking is still fair game, meaning, Apple, among others, is free to collect user behavior data for its own purposes without violating ATT rules.
Nonetheless, these new findings aren’t super surprising. In December 2020, Apple implemented its App Tracking Transparency (ATT) feature, which shines light on the data collection and sharing practices of apps in the App Store and gives users the option of disabling tracking and data sharing when it involves third-parties. However, while ATT can block apps from tracking users across third-party apps and websites, first-party in-app tracking is still fair game, meaning, Apple, among others, is free to collect user behavior data for its own purposes without violating ATT rules.
Beyond ATT, Apple offers a number of different toggles for controlling data collection and usage within iOS and iPadOS. The Privacy & Security page within the settings app contains toggles for location services, ad personalization, and device analytics sharing. The about page for the analytics sharing toggle states that users “may choose to disable the sharing of Device Analytics altogether” (emphasis added).
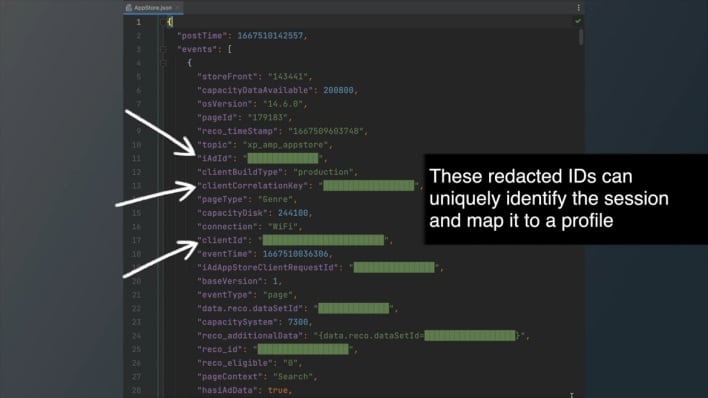
However, iOS developers Tommy Mysk and Talal Haj Bakry found that multiple Apple apps, including the App Store, the iTunes Store, Apple Music, Apple TV, Books, Stocks, send analytics data back to Apple regardless of whether analytics sharing is enabled or disabled in the Settings app. The developers made this discovery on an iPhone running iOS 14.6 that they had jailbroken, enabling them to decrypt requests sent to Apple and read the contents. Mysk and Bakry found that the requests contained multiple unique device identifiers, additional device information, and detailed user behavior information.
The developers analyzed outgoing network traffic on a non-jailbroken iPhone running iOS 16, the latest version of the operating system, and observed Apple apps sending similar requests to Apple. Without jailbreaking the phone, the developers can’t decrypt the requests and confirm that they contain the same user behavior data. Even so, the requests were sent with the same frequency and under the same circumstances as the ones observed on the jailbroken phone, which is good reason to believe that Apple apps on iOS 16 exhibit the same data collection behavior.
However, iOS developers Tommy Mysk and Talal Haj Bakry found that multiple Apple apps, including the App Store, the iTunes Store, Apple Music, Apple TV, Books, Stocks, send analytics data back to Apple regardless of whether analytics sharing is enabled or disabled in the Settings app. The developers made this discovery on an iPhone running iOS 14.6 that they had jailbroken, enabling them to decrypt requests sent to Apple and read the contents. Mysk and Bakry found that the requests contained multiple unique device identifiers, additional device information, and detailed user behavior information.
The developers analyzed outgoing network traffic on a non-jailbroken iPhone running iOS 16, the latest version of the operating system, and observed Apple apps sending similar requests to Apple. Without jailbreaking the phone, the developers can’t decrypt the requests and confirm that they contain the same user behavior data. Even so, the requests were sent with the same frequency and under the same circumstances as the ones observed on the jailbroken phone, which is good reason to believe that Apple apps on iOS 16 exhibit the same data collection behavior.
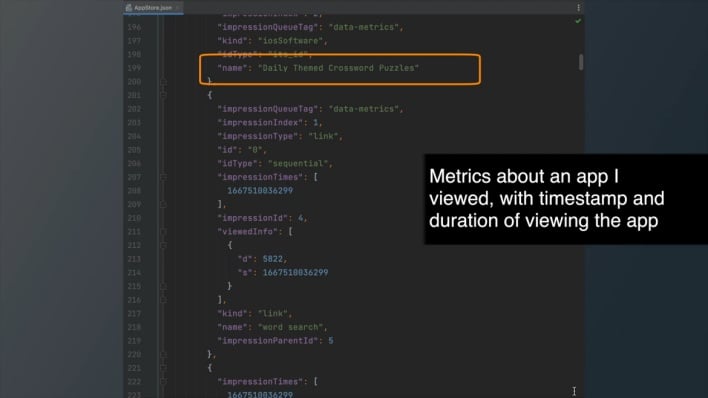
In the case of the App Store, outgoing requests sent to Apple relayed ongoing information about user behavior in real time, including tapped elements, search queries, ads shown, and apps viewed. Perhaps the analytics sharing setting prevents the operating system from sending analytics data to Apple, but not individual Apple apps, meaning the App Store is free to share all this analytics data with Apple separate from the OS. However, the App Store has its own Personalized Recommendations setting, and disabling this setting didn’t change anything about the data sent to Apple either.
Regardless of whether the data collection and usage controls with the operating system and the apps themselves do anything, the developers are of the opinion that the amount of detailed information contained within the analytics data sent to Apple is “too much even if the user has consented to sharing analytics data with Apple.”
Regardless of whether the data collection and usage controls with the operating system and the apps themselves do anything, the developers are of the opinion that the amount of detailed information contained within the analytics data sent to Apple is “too much even if the user has consented to sharing analytics data with Apple.”