BlackRock Android Malware Caught Robbing Private Data From Hundreds Of Popular Apps

New Android malware has surfaced that has an extensive range of data theft capabilities. BlackRock, as the malware is known, has targeted 337 Android applications. The threat was first seen in May and was discovered by security research firm ThreatFabric. According to the research firm, BlackRock is derived from the code of Xerxes banking malware.
Xerxes itself is a strain of the LokiBot Android banking trojan. The code for Xerxes malware was made public around May 2019. The big news for BlackRock is that it has additional features compared to both of its ancestors. Its additional features are particularly focused on the theft of passwords and credit card information.
Functionally, BlackRock works just as most Android banking Trojans do, though it's able to target more apps than its predecessors. The malware can steal login credentials, including usernames and passwords, and can prompt victims to enter payment card details if the targeted apps support financial transactions.
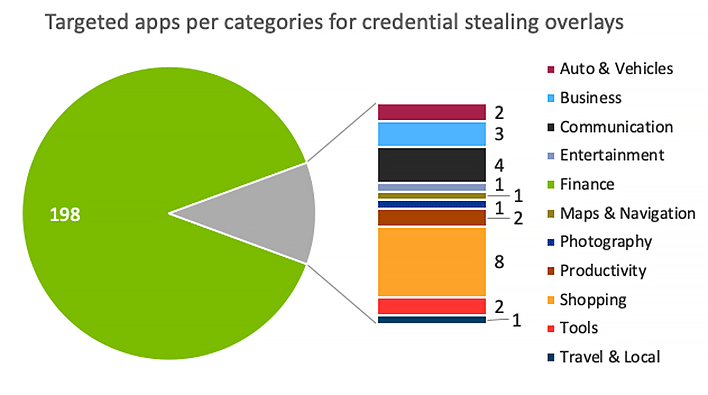
According to ThreatFabric, BlackRock uses overlays that are geared towards phishing data from financial and social media/communications apps. There are overlays meant to phish data from other types of applications including apps for dating, news, shopping, productivity, and lifestyle. The full list of features that the malware leverages to steal user data includes:
- Overlaying: Dynamic (Local injects obtained from C2)
- Keylogging
- SMS harvesting: SMS listing
- SMS harvesting: SMS forwarding
- Device info collection
- SMS: Sending
- Remote actions: Screen-locking
- Self-protection: Hiding the App icon
- Self-protection: Preventing removal
- Notifications collection
- Grant permissions
- AV detection
One notable feature of BlackRock is that once an infected app is installed, it asks the user to grant access to the Accessibility feature allowing it to automate tasks and perform taps on the user's behalf. The Trojan is able to perform the following actions once given Accessibility access:
- Intercept SMS messages
- Perform SMS floods
- Spam contacts with predefined SMS
- Start specific apps
- Log key taps (keylogger functionality)
- Show custom push notifications
- Sabotage mobile antivirus apps, and more
ThreatFabric warns that BlackRock is distributed disguised as a fake Google update package via third-party websites. As of this writing, the trojan hasn't been seen on the official Google Play Store. Earlier this month, the Joker Android malware was seen on the Google Play Store running premium billing scams.

