CISA Tells OEM To Patch Alarming BrakTooth Security Flaws Affecting Billions Of Devices

BrakTooth is a host of security vulnerabilities in commercial Bluetooth stacks that can range from a denial of service to the more serious arbitrary code execution in certain Internet of Things (IoT) devices. The name BrakTooth itself is derived from the word Brak, which means "crash" in Norwegian, and the more obvious tooth which indicates Bluetooth. BrakTooth was first disclosed as a security issue back in April of this year when researchers outlined 16 Bluetooth vulnerabilities discovered on 13 SoC boards from close to a dozen vendors on billions of devices.
After the disclosure it seemed that while some companies (such as Texas Instruments) were able to successfully replicate the security issue, they were not planning on providing any type of patch for it. Others have been selectively applying patches, in that they choose to patch one of their affected products but not another as they play a wait-and-see game concerning BrakTooth. With a list of vulnerable products that includes companies like Qualcomm, Samsung, and Microsoft, this may not come as welcome news to the consumers who own the affected devices.
On November 1st researchers publicly released a tool to test Bluetooth-enabled devices against any potential exploits indicating BrakTooth may be present. It is known as a BrakTooth proof-of-concept (PoC) tool.
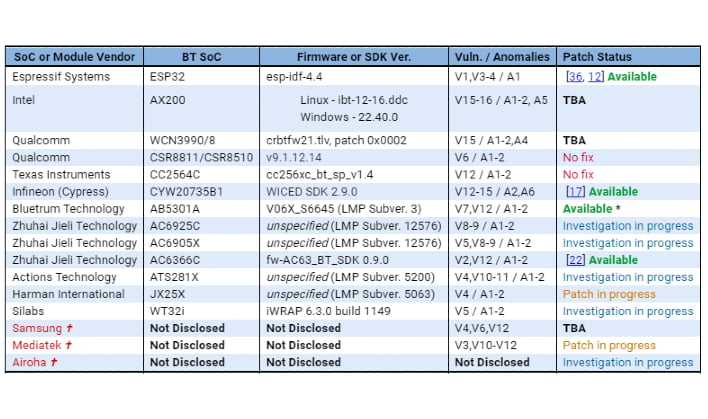
CISA has issued a list of vendors who disclosed to them to be affected by BrakTooth vulnerabilities. At this time it appears only four of those companies have patches available while the others range from "Investigation in progress" to "No fix" as its patch status. See chart below..
The team at CISA said it approached Qualcomm on whether it would be providing a patch for its affected devices. Qualcomm responded by saying it is working on a fix for one, while a second, CSR8811A08, had been fixed since 2011 for ROM versions A12 and beyond. CISA went on to say that new products in 2021 are still being listed to use CSR8811A08, which has no plan on being fixed. It is also worth noting that some of the products that have been identified as being vulnerable are reported to not have enough ROM space to apply a patch.
Anyone with the knowledge on how to exploit the vulnerabilities could do so by using a $15 ESP32 board that can be bought off the shelf, custom Link Manager Protocol (LMP) firmware, and a computer to run the available proof-of-concept (PoC) tool. This is not uncommon as many hacks can be done with fairly inexpensive equipment by those with enough know-how and ingenuity (and lack of a moral compass).
Devices that could be affected by Braktooth include smartphones, computers, audio devices, toys, IoT gadgets, and industrial equipment. It is no surprise with a list that includes devices that we carry with us everyday with our sensitive data on it that the CISA is once again encouraging companies to come up with patches and/or workarounds for any and all vulnerabilities associated with BrakTooth. Hopefully this time around more companies will take notice and stop playing games with the products consumers have bought from them with a level of trust that includes protecting them from known security issues.