Sneaky Emotet Trojan Uses Sophisticated Methods To Load Malware, Spread Via Wi-Fi Networks

A new trojan has been spotted that is called Emotet. The trojan is described as highly sophisticated and it serves as a loader for other malware or ransomware once installed on a system. The key function of Emotet is that it can deliver custom modules or plugins that are designed for specific tasks. Those tasks include things like stealing Outlook contacts or spreading over a LAN.
Recently, Binary Defense discovered a new loader type that takes advantage of the wlanAPI interface to enumerate all WiFi networks in the area. It will then attempt to spread to those networks and infect all the devices it can as it spreads. The protocol for the trojan is based on Google's Protobufs to serialize data to and from the server. Emotet uses brute force attacks and insecure passwords to jump from WiFi network to WiFi network.
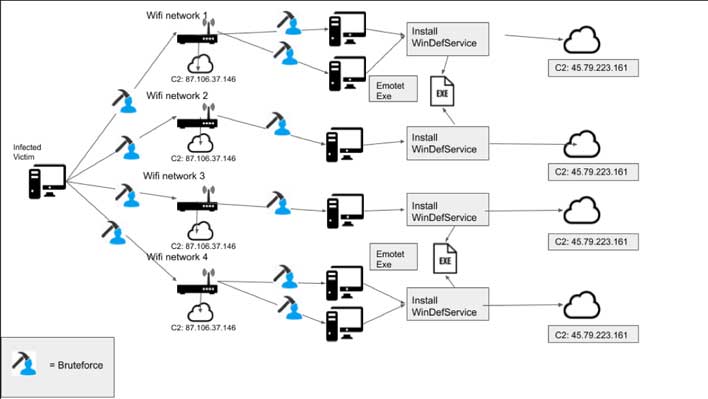
Other than stealing Outlook contacts, the trojan can also steal personal information, install ransomware, download other malware, and form botnets. Researchers say that Emotet is relatively easy to defeat by using strong network passwords. Designers of the Trojan gave it a common set of passwords that people frequently use for their WiFi networks. Once it is successful in discovering the password, the working password is sent to a command-and-control server to be added to the master list.
Emotet also uses brute force to get into Windows devices that it finds on the LAN or WiFi network. Binary Defense says that keeping the trojan off your networks is easily done by using strong passwords. Users could also roll out network monitoring to secure the network further. Any network with a weak password that is commonly used or a network that is using the default password for the modem or router is at risk.
In other malware news, recently a macOS malware called Shlayer that leverages Adobe Flash was seen making the rounds.

