Nasty Escobar Banking Trojan Is Targeting Google Authenticator Codes For Android

With the package name of com.escobar.pablo, the malware includes a number of the same features and code as another one named Aberebot. Researchers at Cyble, a security research organization, found the malware by scouring a cybercrime-oriented forum. The feature set includes remote view, phishing overlays, screen captures, text-message captures, and even multi-factor authentication capture.
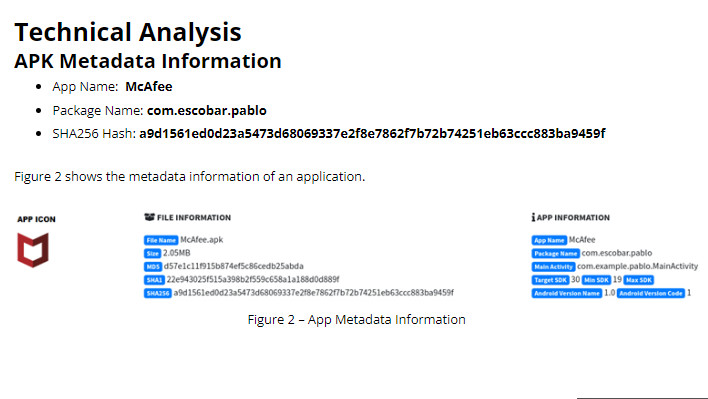
All of those features are used in tandem with an attempt to steal a user's banking information. This malware even goes so far as to disguise itself as McAfee antivirus software, and even uses the McAfee logo as its icon. Masquerading as security software is nothing new—in fact, we recently reported on malware that was packaged directly inside of a fully functioning 2-factor authentication app.
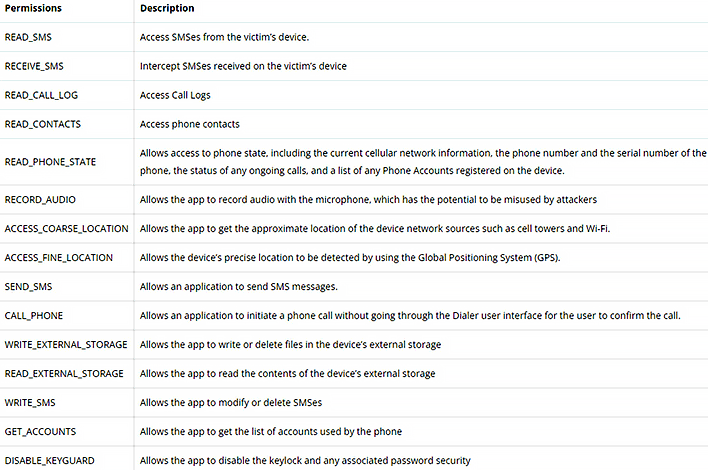
The full list of dangers of this particular malware is extensive. Not only can it do what was outlined above. It can also bypass your screen lock and even send text messages to your entire contact list. It also can record audio from the microphone, get your location, and initiate phone calls. The malware even has the capability of checking the phone's access to data, such as if you turned off mobile data and turn it back on again.
The absolute biggest threat though is that it can even read from the official Google Authenticator app, without user interaction, by directly interfacing with it to capture any codes that might be used during a login process.
How can you protect yourself from such a nasty piece of work? Well, so far the malware does not look to have been included in any official distribution via the Play Store. So don't do any side-loading of APKs that you don't trust, or don't side-load at all. Watch your mobile and Wi-Fi data on your device and if there are any apps you don't recognize using extra data, look into them.
If you have any legitimate malware detecting apps, pay attention to their notices. If you believe you've been infected, unfortunately, the best way to eradicate is a factory reset. So, run a backup of anything you deem important on your device (be careful not to include the malware of course) and run your factory reset. The researchers even recommend removing your SIM card because of the data interaction and capabilities of this app to re-activate your mobile data connection without user interaction.