Google Chrome Users, Update ASAP To Fix These Actively Exploited Zero-Day Security Flaws
Have you updated your Chrome browser lately? Assuming you use Chrome, now would be a good time to force the issue, as the latest update brings with it patches for nearly a dozen security flaws, including a pair of zero-day vulnerabilities that Google says are actively being exploited in the wild. So, yeah, take two seconds to update your browser.
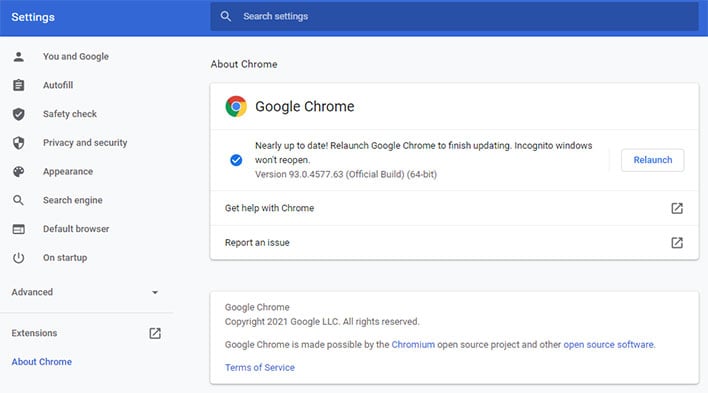
The latest Chrome release for Windows, Mac, and Linux is 93.0.4577.82. Chrome does a good job of updating itself, and in this case, Google says the latest version will roll out to PCs over the coming days and weeks. You don't necessarily have to wait, however, you can have Chrome manually fetch the update right now.
To do that, click the three vertical dots in the upper-right corner of the browser, then navigate to Help > About Google Chrome. This prompts Chrome to look for any updates and, if available, it will download them and prompt you to relaunch the browser to install the patches. Your open browser windows and tabs will reload, but be sure to save any browser-based work you might have going on (like an article in a CMS).
It doesn't take long, and you'll have a more secure browser afterward.
"This update includes 11 security fixes...Google is aware that exploits for CVE-2021-30632 and CVE-2021-30633 exist in the wild," Google stated in the release notes.
Both of those were disclosed to Google last week. For the time being, details about those and the other nine vulnerabilities that are patched with the latest build are still under lock and key by Google, which will share more information once "a majority of users are updated with a fix."
According to the release notes, CVE-2021-30632 refers to an out-of-bounds write flaw in the V8 JavaScript engine that lead to data corruption or unwanted code execution, while CVE-2021-30633 is in reference to a user-after-free exploit in the IndexedDB API that can be used for a variety of attacks, including remote code execution.
Here's a full list, along with their accompanying bug bounties...
- [$7500][1237533] High CVE-2021-30625: Use after free in Selection API. Reported by Marcin Towalski of Cisco Talos on 2021-08-06
- [$7500][1241036] High CVE-2021-30626: Out of bounds memory access in ANGLE. Reported by Jeonghoon Shin of Theori on 2021-08-18
- [$5000][1245786] High CVE-2021-30627: Type Confusion in Blink layout. Reported by Aki Helin of OUSPG on 2021-09-01
- [$TBD][1241123] High CVE-2021-30628: Stack buffer overflow in ANGLE. Reported by Jaehun Jeong(@n3sk) of Theori on 2021-08-18
- [$TBD][1243646] High CVE-2021-30629: Use after free in Permissions. Reported by Weipeng Jiang (@Krace) from Codesafe Team of Legendsec at Qi'anxin Group on 2021-08-26
- [$TBD][1244568] High CVE-2021-30630: Inappropriate implementation in Blink . Reported by SorryMybad (@S0rryMybad) of Kunlun Lab on 2021-08-30
- [$TBD][1246932] High CVE-2021-30631: Type Confusion in Blink layout. Reported by Atte Kettunen of OUSPG on 2021-09-06
- [$TBD][1247763] High CVE-2021-30632: Out of bounds write in V8. Reported by Anonymous on 2021-09-08
- [$TBD][1247766] High CVE-2021-30633: Use after free in Indexed DB API. Reported by Anonymous on 2021-09-08
The tally so far adds up to $20,000 in bounties, though Google is still determining amounts for eight of the bugs. Kudos to the researchers who discovered the vulnerabilities, and congrats on the payday.