Login Flow Faux Pas Enabled Twitter's 5 Million Account Data Leak That Sold For $30K

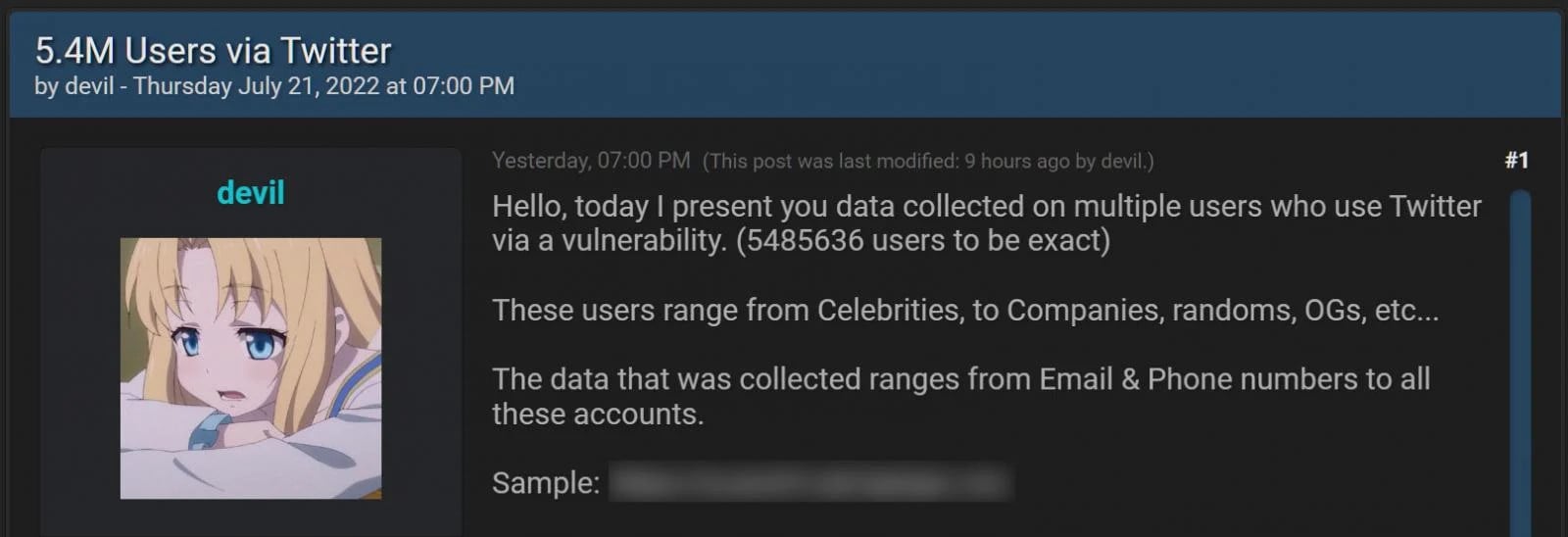
The sad security news for Twitter is that the information of more than 5.4 million users was gained through an exploit reported to Twitter via its bug bounty program back in January of 2022. At the time of the report, though, Twitter claims they had no indication that the exploit was being taken advantage of. However, the person who is offering up the data says it was gathered in December of 2021, a month before the vulnerability was reported. This is not even the latest in additional Twitter drama which recently experienced an outage to its entire system.
The exact method of the exploit was not explicitly outlined, but basically, it looks to have come through an account recovery process or just the login process itself. Twitter fixed the exploit as soon as it was reported. Effectively it allowed anyone who used the exploit to get the e-mail address, phone number, or Twitter ID from the login process. The hacker who is offering up the data is asking for $30k from each interested party, and claims they've already received some offers.
The source of the flaw was a login flow practice long advised against. When an invalid login attempt is made, the system should not disclose whether or not an account with that name exists. While this can lead to some user frustration when they cannot remember if they are entering their correct user ID, it prevents bad actors from compiling a list of accounts to target brute force or social engineering attacks against. In Twitter's case, the login process was going beyond revealing the existence of an account on a failed login attempt. The loophole enabled attackers to enter series of phone numbers or e-mail addresses and discover associated accounts. This has broader implications of potentially revealing the identities of pseudonymous users on the platform.
Twitter's public response is to reach out to each user they know was likely affected. It also reminds users to enable 2-factor authentication using apps or hardware security keys. While there is no indication of password theft, there is the usual advice for those who were affected or feel like they may have been to reset or set new passwords for their accounts.