Security Firm Warns These Major UEFI BIOS Security Flaws Affect Millions Of Devices
A team from Binarly, a firmware protection company, recently discovered several repeatable anomalies on twenty different enterprise machines in the course of a job for a midsize enterprise company. After looking further into these anomalies and digging all the way down into the disassembly code, the team found 23 critical Unified Extensible Firmware Interface (UEFI) vulnerabilities ripe for exploitation.
These vulnerabilities were traced back to Insyde Software’s InsydeH2O UEFI firmware framework code. Over 25 vendors have been using this framework code as part of an Insyde-based firmware SDK to develop firmware. The list of vendors includes Fujitsu, Siemens, Dell, HP, HPE, Lenovo, Microsoft, Intel, and Bull Atos.
These vulnerabilities were traced back to Insyde Software’s InsydeH2O UEFI firmware framework code. Over 25 vendors have been using this framework code as part of an Insyde-based firmware SDK to develop firmware. The list of vendors includes Fujitsu, Siemens, Dell, HP, HPE, Lenovo, Microsoft, Intel, and Bull Atos.
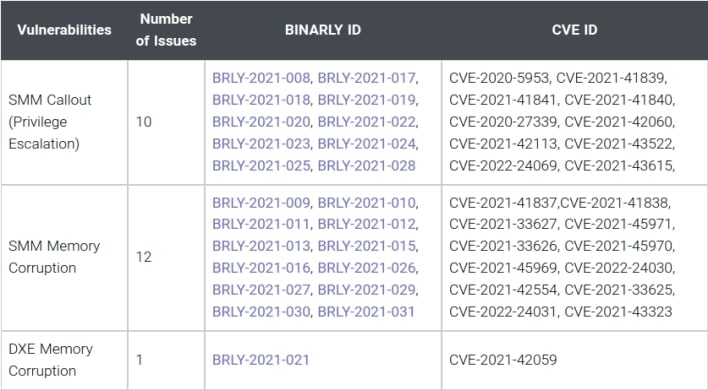
All but one of the vulnerabilities involve System Management Mode (SMM), with the odd one out being a memory corruption vulnerability in InsydeH2O’s Driver eXecution Environment (DXE). All of the SMM vulnerabilities can lead to a particularly nasty form of privilege escalation, given that SMM privileges exceed those of root or administrator, as SMM operates below the level of the operating system.
As a result, attackers who exploit these vulnerabilities to achieve SMM privilege escalation could bypass boot security features and implant persistent malware. We recently reported on one such persistent malware dubbed MoonBounce. MoonBounce is a rootkit that can be embedded where firmware resides on flash memory, enabling the malware to survive an OS reinstall, a drive format, or even a drive replacement.
Given the severe threat of SMM privilege escalation and the possibility for persistent malware, which is difficult both to detect and remove, these vulnerabilities have high severity ratings. They all have scores of 7.5 or 8.2 in the Common Vulnerability Scoring System (CVSS) Version 2.0, but three of them are listed in the National Vulnerability Database (NVD) as critical vulnerabilities with scores of 9.8 in CVSS Version 3.x.
Fortunately, the Binarly team privately disclosed these vulnerabilities back in September of 2021, and Insyde Software has already released firmware updates that patch all 23 of the vulnerabilities. That said, it will take some time for the affected vendors to adopt these updates and push them out in security updates for end-users, and some products may never receive these updates.
Binarly has released FwHunt rules for detecting the vulnerabilities on GitHub, and you can read more about the vulnerabilities in Binarly’s in-depth post.
As a result, attackers who exploit these vulnerabilities to achieve SMM privilege escalation could bypass boot security features and implant persistent malware. We recently reported on one such persistent malware dubbed MoonBounce. MoonBounce is a rootkit that can be embedded where firmware resides on flash memory, enabling the malware to survive an OS reinstall, a drive format, or even a drive replacement.
Given the severe threat of SMM privilege escalation and the possibility for persistent malware, which is difficult both to detect and remove, these vulnerabilities have high severity ratings. They all have scores of 7.5 or 8.2 in the Common Vulnerability Scoring System (CVSS) Version 2.0, but three of them are listed in the National Vulnerability Database (NVD) as critical vulnerabilities with scores of 9.8 in CVSS Version 3.x.
Fortunately, the Binarly team privately disclosed these vulnerabilities back in September of 2021, and Insyde Software has already released firmware updates that patch all 23 of the vulnerabilities. That said, it will take some time for the affected vendors to adopt these updates and push them out in security updates for end-users, and some products may never receive these updates.
Binarly has released FwHunt rules for detecting the vulnerabilities on GitHub, and you can read more about the vulnerabilities in Binarly’s in-depth post.

