Massive Cyberattack Campaign Targets 1.6M WordPress Sites For Vulnerable Plugins

WordPress is one of the most popular and thus commonly used content management systems (CMS) on the web. However, it has a particular problem with add-on, extension, and plug-in authors abandoning their projects, and subsequently leaving gaping holes in site security. A case in point has been highlighted by the Wordfence blog this week, which discusses a severe vulnerability that users of the Kaswara Modern WPBakery Page Builder Addons are now prey to.
The Kaswara Addon was abandoned by its author before an arbitrary file upload vulnerability, tracked as CVE-2021-24284, came to light—and therefore it has never been patched. WordPress users who are not vigilant, or don’t pay anyone or for any service to be vigilant for them, can easily fall behind on core and extension updates. Moreover, some plugins become obsolete, or can be replaced by new inbuilt functionality or much better solutions as time and technology moves forward. Kaswara Modern WPBakery Page Builder Addons have a vulnerability that allows for something very bad—it can be used as a route “to upload malicious PHP files to an affected website, leading to code execution and complete site takeover.” Of course that might be just the beginning of a very slippery downward slope for your website’s content, ranking, and reputation.
It is recommended that any users of Kaswara Modern WPBakery Page Builder Addons deactivate and then purge them ASAP. An alternative modern and regularly updated addon with similar functionality can be sought if it is needed. Even if you have this addon and it is not activated on your site, it should still be deleted.
While sites like HotHardware are now making the knowledge about this addon vulnerability mainstream, it has been well known by threat actors for 10 or 11 days. Wordfence notes that it has blocked nearly half a million attack attempts a day since early July, attacks which unprotected sites with this addon would fall victim to. The makers of Wordfence say that roughly 1.6M sites under its protection have been targeted repeatedly by attackers seeking out this vulnerability.
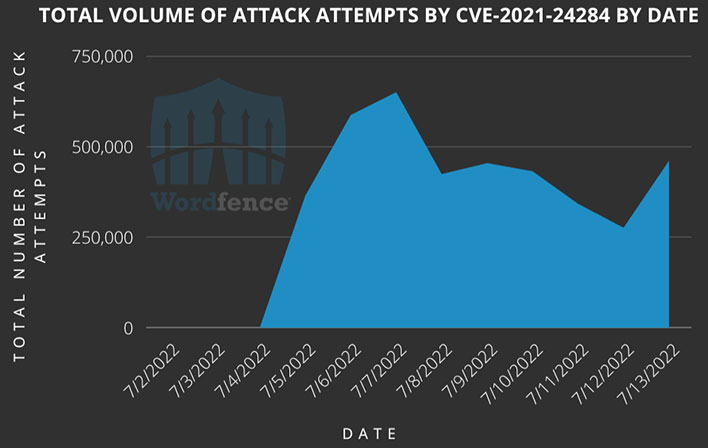
Of course, Wordfence promotes its plugin in the blog post regarding Kaswara Modern WPBakery Page Builder Addons and CVE-2021-24284. However, it is quite justified in doing so, given that users of the Wordfence plugin for WordPress, even the free tier, have had protection against the CVE-2021-24284 vulnerability since mid-May.
You can read more about the Kaswara Modern WPBakery Page Builder Addons, CVE-2021-24284, and Wordfence via the source blog post. Also, the blog lists the top 10 IP addresses from where exploits for CVE-2021-24284 are attempted, which is useful if you wish to blacklist them from access to your WordPress site.

