Google's Sloppy Approach To Browser Extensions Leaves You Vulnerable To Password Theft

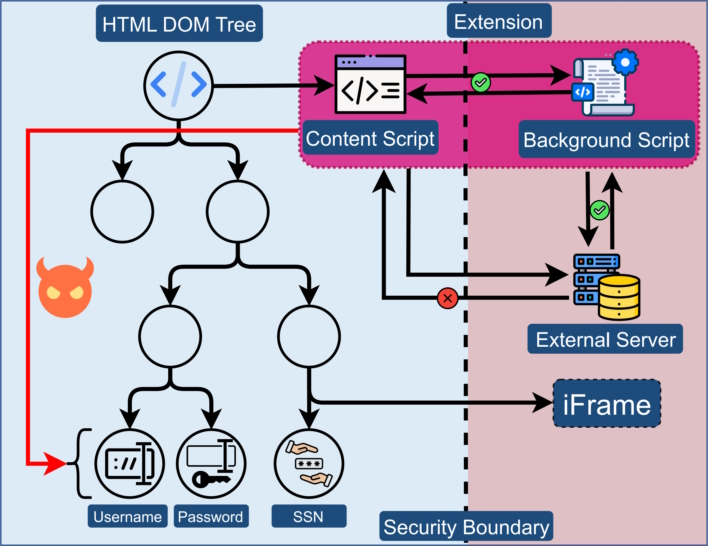
The research, published on August 30th, explains that the problem lies with browser extensions and how permissions are traditionally handled. The current permissions system found across all browsers is a “coarse-grained approach, particularly with respect to access to web page content.” This means that once an extension is loaded onto a page, it has access to all elements. The researchers further explain that this lack of a security boundary could allow an extension to access and even maybe manipulate data in any input field on a webpage.
In December 2020, Google introduced Manifest V3, a change to the extensions platform, to close security loopholes and improve privacy and performance. Despite this, the researchers were able to create an extension that would extract sensitive input field values, which they were then able to upload to the Google Chrome web store as a ChatGPT-like assistant. While this extension was left as ‘unpublished’ in the store and was ethically handled, it still goes to show that it may not take much to upload a malicious browser extension.
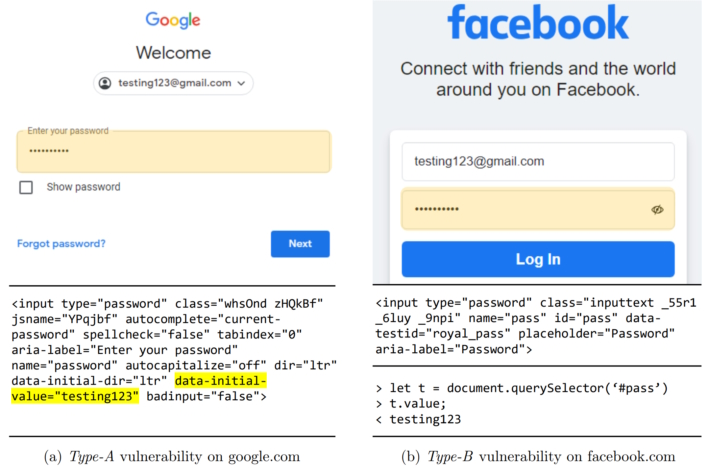
Following this success, the team sought to find sites that may be vulnerable to this kind of attack, scanning the top 10K websites. They found that 7,140 of these websites had password fields that could have data extracted, including Google, Cloudflare, Facebook, and others. The researchers further looked at what extensions could possibly abuse this and found that 12.5% or over 17,000 extensions have permission to extract information from all web pages.
At the end of the day, the researchers’ work shows that there is a systemic issue at hand that could put internet users at risk of having compromised accounts if that has not happened already. While there is a proposed solution for developers, end users should know and trust all of their extensions just as they would any other software. However, hopefully, this will not be much of a problem if proper security measures are implemented.