SeaFlower Hackers Steal Crypto With Secret Backdoors In Your Android And iOS Wallets

Last week, the US Federal Trade Commission (FTC) published a report according to which cryptocurrency scammers have swindled Americans out of over $1 billion since 2021. Cryptocurrency scams are rampant on social media sites, as well as messaging apps like Telegram. The scams often trade on the names of cryptocurrency-related celebrities, such as Jack Dorsey and Elon Musk. However, scams are just one way for bad actors to steal cryptocurrency. Rather than tricking unsuspecting victims into handing over their cryptocurrency, some cybercriminals instead turn to malware in order to poach cryptocurrency themselves.
Researchers from Confiant have published their findings detailing an extensive malware campaign the researchers are calling SeaFlower. The campaign is targeted at users of four different cryptocurrency wallets on iOS and Android: MetaMask, Coinbase Wallet, imToken Wallet, and TockenPocket Wallet. The threat actors behind SeaFlower to speak Chinese, judging by code comments written in Chinese, along with a number of other indicators noted by the researchers. The threat actors also appear to be targeting other Chinese speakers most heavily, having conducted an SEO poisoning campaign that has most affected search results from the Chinese-based Baidu search engine. SEO poisoning campaigns leverage search engine optimization (SEO) techniques to boost malicious websites into the top search results for legitimate websites or services.
Researchers from Confiant have published their findings detailing an extensive malware campaign the researchers are calling SeaFlower. The campaign is targeted at users of four different cryptocurrency wallets on iOS and Android: MetaMask, Coinbase Wallet, imToken Wallet, and TockenPocket Wallet. The threat actors behind SeaFlower to speak Chinese, judging by code comments written in Chinese, along with a number of other indicators noted by the researchers. The threat actors also appear to be targeting other Chinese speakers most heavily, having conducted an SEO poisoning campaign that has most affected search results from the Chinese-based Baidu search engine. SEO poisoning campaigns leverage search engine optimization (SEO) techniques to boost malicious websites into the top search results for legitimate websites or services.
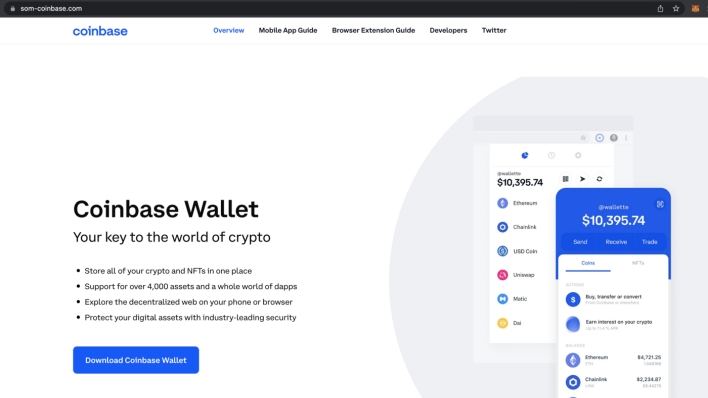
In this case, the threat actors have successfully boosted malicious clones of websites for legitimate cryptocurrency wallet. The malicious websites appear identical to their legitimate counterparts, but are hosted at domains controlled by the threat actors. The malicious websites include download buttons for Android and iOS apps, but, rather than redirecting users to the Google Play Store or the Apple App Store, the buttons instead attempt to side-load apps onto users’ devices.
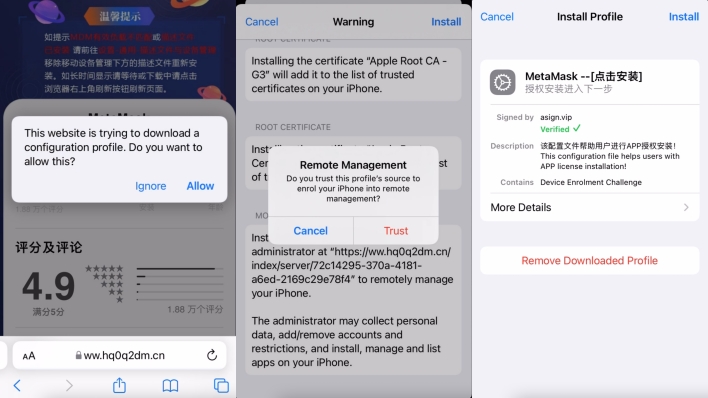
In the case of Android, the websites simply serve up an APK file, which users can download and install themselves. However, Apple doesn’t allow for easy app side-loading like on Android, so, rather than serving up an installation package, the websites instead attempt to set up a provisioning profile on iOS devices. These profiles come with developer keys that allow for the side-loading of the malicious apps.
Once installed, the malicious apps appear and function identically to the legitimate cryptocurrency wallet apps they mimic. However, the malicious apps come with backdoors that log the wallet seed phrases, addresses, and balances and send that information to the threat actors behind the campaign. The threat actors can then use the seed phrases to carry out the account recovery process and gain access to the funds in victims’ wallets. In some cases, the code containing the backdoors is encrypted, meaning anyone inspecting the code for malicious behavior must first use the included cryptographic keys to decrypt the malicious code before discovering what the code does.
In order to avoid falling prey to a malicious app campaign such as this one, iOS users should never allow outside provisioning profiles to be installed on their devices, and Android users should install apps only from trusted sources. All of the wallet apps targeted by this particular attack can be found in the Google Play Store and Apple App Store, so users should download and install them there.
The researchers have provided the hashes for one of the malicious Android apps and all four malicious iOS apps distributed as part of the SeaFlower campaign, so others can identify the malicious apps.
Coinbase Wallet Android app
SHA-256 of the APK:
83dec763560049965b524932dabc6bd6
Once installed, the malicious apps appear and function identically to the legitimate cryptocurrency wallet apps they mimic. However, the malicious apps come with backdoors that log the wallet seed phrases, addresses, and balances and send that information to the threat actors behind the campaign. The threat actors can then use the seed phrases to carry out the account recovery process and gain access to the funds in victims’ wallets. In some cases, the code containing the backdoors is encrypted, meaning anyone inspecting the code for malicious behavior must first use the included cryptographic keys to decrypt the malicious code before discovering what the code does.
In order to avoid falling prey to a malicious app campaign such as this one, iOS users should never allow outside provisioning profiles to be installed on their devices, and Android users should install apps only from trusted sources. All of the wallet apps targeted by this particular attack can be found in the Google Play Store and Apple App Store, so users should download and install them there.
The researchers have provided the hashes for one of the malicious Android apps and all four malicious iOS apps distributed as part of the SeaFlower campaign, so others can identify the malicious apps.
Coinbase Wallet Android app
SHA-256 of the APK:
83dec763560049965b524932dabc6bd6
252c7ca2ce9016f47c397293c6cd17a5
Coinbase Wallet iOS app
SHA-256 of the .IPA analyzed:
2334e9fc13b6fe12a6dd92f8bd65467cf
Coinbase Wallet iOS app
SHA-256 of the .IPA analyzed:
2334e9fc13b6fe12a6dd92f8bd65467cf
700f43fdb713a209a74174fdaabd2e2
MetaMask iOS app
SHA-256 .IPA file analyzed:
9003d11f9ccfe17527ed6b35f5fe33d28
MetaMask iOS app
SHA-256 .IPA file analyzed:
9003d11f9ccfe17527ed6b35f5fe33d28
e76d97e2906c2dbef11d368de2a75f8
imToken Wallet iOS app
SHA-256 of the .IPA analyzed:
1e232c74082e4d72c86e44f1399643ff
imToken Wallet iOS app
SHA-256 of the .IPA analyzed:
1e232c74082e4d72c86e44f1399643ff
b6f7836805c9ba4b4235fedbeeb8bdca
TokenPocket iOS Wallet
SHA-256 of the .IPA file analyzed:
46002ac5a0caaa2617371bddbdbc7eca
TokenPocket iOS Wallet
SHA-256 of the .IPA file analyzed:
46002ac5a0caaa2617371bddbdbc7eca
74cd9cb48878da0d3218a78d5be7a53a

