Snake Keylogger Slithers Onto PCs With Malicious Word Docs In Sinister Malware Campaign
According to the report, the victim would receive an e-mail with a subject line of "Remittance Invoice," which likely would look like it could be an invoice. The PDF format is often used for invoices, quotes, and other business interactions and files due to it's perceived increased security. Unfortunately in this case, the file is less than secure.
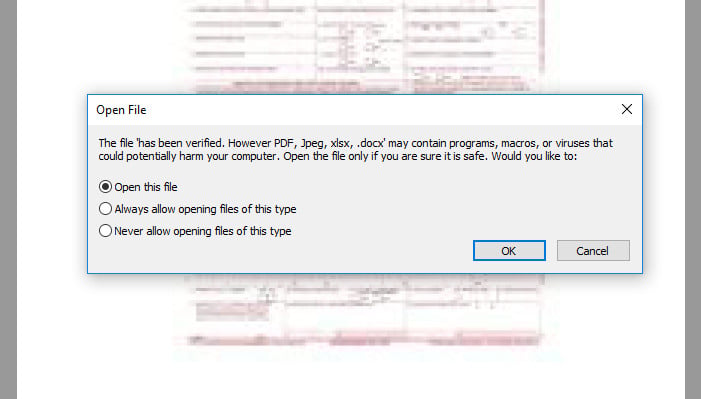
This file is less secure because it houses a hidden Microsoft Office document, typically a Word DOCX file. The embedded file has the name "has been verified." When the user sees the prompt of Adobe PDF attempting to open the file the dialogue reads ,"The file 'has been verified'." as the first statement in the prompt, which the attacker hopes that the victim will just allow the system to bypass. Unfortunately, a bit of simple trickery which happens to work all too well on many users.
As with any malware threat, becoming infected can be rather serious. However, this particular threat has some pretty low chances of infection overall. In February Microsoft started rolling out updates to newer versions of Office that prevents macros from being loaded automatically without prompt. The security flaw that this end result exploits is already patched. So in order to actually become infected the user would need to be on an unpatched system, unwitting or unwary, open the PDF, allow the PDF to run, and bypass the macro prevention. Quite a lot of variables there, but, this malware was detected by HP Wolf this year, so it doesn't mean it can't happen.