Sinister Mac Malware Strain Returns With A Clever Trick To Dupe Apple Users

This new and potent version of XLoader is written in the C and Objective C programming languages under the guise of being an office productivity app called ‘OfficeNote.’ It is bundled in a standard Apple disk image and was signed with an Apple developer signature, though Apple has since revoked the signature. However, Apple’s antivirus tool, xProtect, does not reportedly have the means to prevent the malware from running, meaning XLoader can fly under the radar and steal information with relative ease.
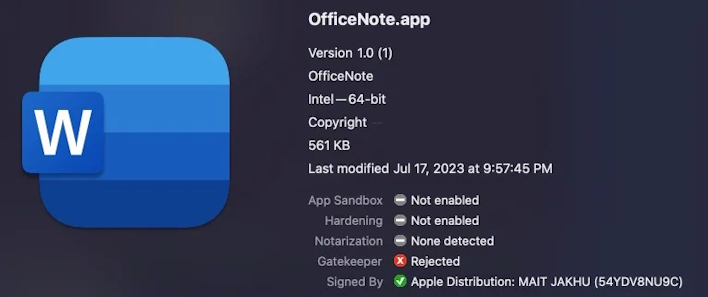
The researchers at SentinelOne also noted that this malware has seemingly been widely distributed after becoming available on ‘crimeware’ forums for rent, costing anywhere from $199 a month to $299 for three months. For this price, a threat actor can steal secrets from a victim’s clipboard, steal login information from Firefox and Chrome, and join the compromised device to the threat actor's command and control (C2) network.
As Apple is currently not detecting this malware, it is recommended that users have a trusted third-party security solution to detect and protect against malware like XLoader. Further, users should know and trust what they are installing before installing it, and while this may be difficult with valid developer signatures, some research may prevent malware like this from taking off.

