HP Warns Of Tricky RedLine Stealer Malware Masquerading As Windows 11 Installers
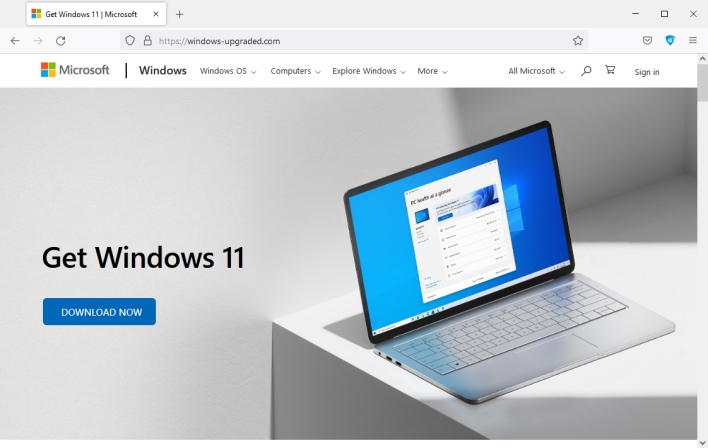
HP, which maintains a threat analyst team, has released a post on its threat research blog detailing a tricky new malware campaign. Only a day after Microsoft announced that Windows 11 was entering its final phase of availability, becoming available for broad deployment on eligible devices, HP discovered that someone with registration information pointing to Moscow, Russia had newly registered the domain windows-upgraded[.]com.
This newly registered domain pointed to a website that copied the look of a legitimate Microsoft website. Users who visited the site would find a button prompting them to download a Windows 11 installer. Clicking on the button would download a file labeled Windows11InstallationAssistant.zip that was hosted on Discord’s content delivery network.
The suspicious zip file is only 1.5MB, which expands to 753MB when unzipped. 751 of those megabytes make up an executable named Windows11InstallationAssistant.exe. The other two megabytes compose six different Windows DLLs and an XML file. Compressing the entire 753MB package down to only 1.5MB requires a compression ratio of 99.8%, which is very high compared to the average zip compression ratio for executables of 47%.
This high compression ratio is achieved by padding a large part of the executable file with easily compressible 0x30 bytes. This padding expands the uncompressed size of the executable beyond the size that many malware analysis tools are able to process. As a result, the malicious executable may avoid detection by anti-virus software, leaving unsuspecting users free to execute the file.
This newly registered domain pointed to a website that copied the look of a legitimate Microsoft website. Users who visited the site would find a button prompting them to download a Windows 11 installer. Clicking on the button would download a file labeled Windows11InstallationAssistant.zip that was hosted on Discord’s content delivery network.
The suspicious zip file is only 1.5MB, which expands to 753MB when unzipped. 751 of those megabytes make up an executable named Windows11InstallationAssistant.exe. The other two megabytes compose six different Windows DLLs and an XML file. Compressing the entire 753MB package down to only 1.5MB requires a compression ratio of 99.8%, which is very high compared to the average zip compression ratio for executables of 47%.
This high compression ratio is achieved by padding a large part of the executable file with easily compressible 0x30 bytes. This padding expands the uncompressed size of the executable beyond the size that many malware analysis tools are able to process. As a result, the malicious executable may avoid detection by anti-virus software, leaving unsuspecting users free to execute the file.
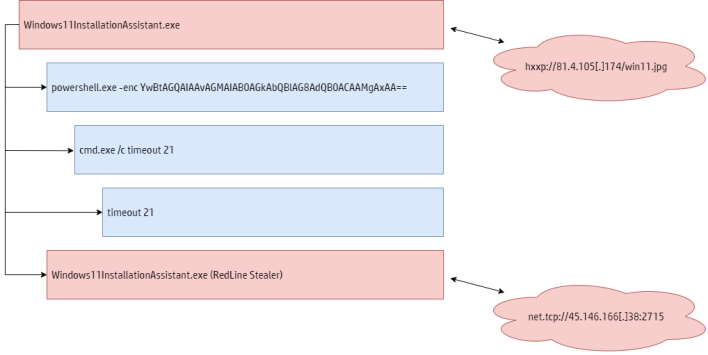
Once the executable runs, it starts a PowerShell process with an encoded argument that launches a cmd.exe process with a timeout of 21 seconds. After 21 seconds pass, the initial process fetches a file titled win11.jpg from a remote server. This new file is not actually a JPEG image file, but rather contains a DLL file stored in reverse order.
The initial process reverses the contents of the newly fetched file and loads the resulting DLL file, which turns out to the RedLine Stealer malware. This malware collects information such as usernames, computer names, installed software, hardware information, passwords stored in web browsers, auto-complete data such as credit card information, and cryptocurrency wallets.
This new Windows 11 installer malware campaign mirrors another campaign that HP recently analyzed in which the malicious actor disguised the malware as an installer for the Discord app. The malicious actor registered discrodappp[.]com with the same domain registrar, used the same DNS servers, and delivered the same family of malware as in this new Windows 11 installer campaign.
The HP blog post on this new campaign contains further details.
The initial process reverses the contents of the newly fetched file and loads the resulting DLL file, which turns out to the RedLine Stealer malware. This malware collects information such as usernames, computer names, installed software, hardware information, passwords stored in web browsers, auto-complete data such as credit card information, and cryptocurrency wallets.
This new Windows 11 installer malware campaign mirrors another campaign that HP recently analyzed in which the malicious actor disguised the malware as an installer for the Discord app. The malicious actor registered discrodappp[.]com with the same domain registrar, used the same DNS servers, and delivered the same family of malware as in this new Windows 11 installer campaign.
The HP blog post on this new campaign contains further details.

