Beware Of Roaming Mantis Malware Phishing Campaign Preying On Android And iOS Users

While malware and phishing are two different kinds of cyberattacks, threat actors sometimes use both methods in malicious campaigns. A threat actor known as Roaming Mantis appears to be doing exactly that in a new campaign documented by researchers at the cybersecurity firm SEKOIA. Roaming Mantis has previously targeted users in Japan, South Korea, Taiwan, Germany, France, the UK, and the US, distributing the MoqHao Android malware, also known as XLoader. The researchers estimate that this new campaign has compromised around 70,000 Android devices belonging to French users.
Similar to a spyware campaign recently targeting Italian users, the campaign’s kill chain begins with an SMS message sent to phone numbers beginning with France’s +33 country code. The text message tells recipients that a package has been sent that requires review. The message includes a malicious link that directs users to different destinations, depending on certain conditions. If the user’s IP address corresponds to a location outside of France, the user is sent a 404 error, ending the attack prematurely.
Similar to a spyware campaign recently targeting Italian users, the campaign’s kill chain begins with an SMS message sent to phone numbers beginning with France’s +33 country code. The text message tells recipients that a package has been sent that requires review. The message includes a malicious link that directs users to different destinations, depending on certain conditions. If the user’s IP address corresponds to a location outside of France, the user is sent a 404 error, ending the attack prematurely.
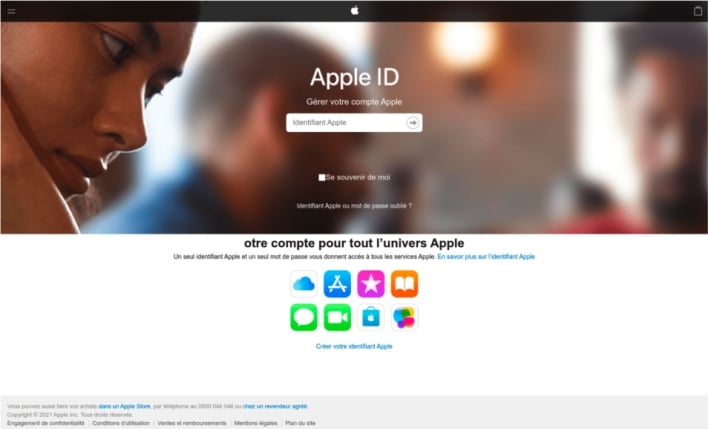
However, if the user has a French IP address, the malicious server then detects the mobile device operating system. In the case of an Apple device running iOS, the server sends the victim to a phishing page that mimics the French-language Apple ID login page. Any Apple ID user credentials entered into this page are obtained by the Roaming Mantis threat actor for later use.
If the victim’s phone is running Android, the server redirects the victim to a page that displays an alert and attempts to download an APK file. If the victim runs the APK file and disables the Android safeguards that protect against installing apps from unknown sources, it installs a malicious app that mimics the Chrome browser and asks victims to grant it extensive permissions. The XLoader malware contained within the app connects to the legitimate image hosting service Imgur to retrieve a command-and-control (C2) configuration from a user profile. The malware then steals information from the infected device and uploads it to the C2 server.
Between the phishing attack targeting iOS users and the malware attack targeting Android users, Roaming Mantis is able to gain access to a large range of personal data, as well as remotely interact with victims’ devices. This sensitive data and remote access could later be used to aid in extortion of the victims or associated businesses and institutions.
If the victim’s phone is running Android, the server redirects the victim to a page that displays an alert and attempts to download an APK file. If the victim runs the APK file and disables the Android safeguards that protect against installing apps from unknown sources, it installs a malicious app that mimics the Chrome browser and asks victims to grant it extensive permissions. The XLoader malware contained within the app connects to the legitimate image hosting service Imgur to retrieve a command-and-control (C2) configuration from a user profile. The malware then steals information from the infected device and uploads it to the C2 server.
Between the phishing attack targeting iOS users and the malware attack targeting Android users, Roaming Mantis is able to gain access to a large range of personal data, as well as remotely interact with victims’ devices. This sensitive data and remote access could later be used to aid in extortion of the victims or associated businesses and institutions.

