AMD Discloses 31 New Ryzen And EPYC CPU Vulnerabilities And Security Patch Strategy

Each vulnerability is labeled as High, Medium, and Low severity. One particularly nasty vulnerability that affects both consumer and server processors has a label of CVE-2021-26316. Its description indicates that there is a failure of validation in the communication buffer and communication service in BIOS that "may allow an attacker to tamper with the buffer resulting in potential System Management Mode arbitrary code execution." This seems to affect just about all the CPUs in the list.
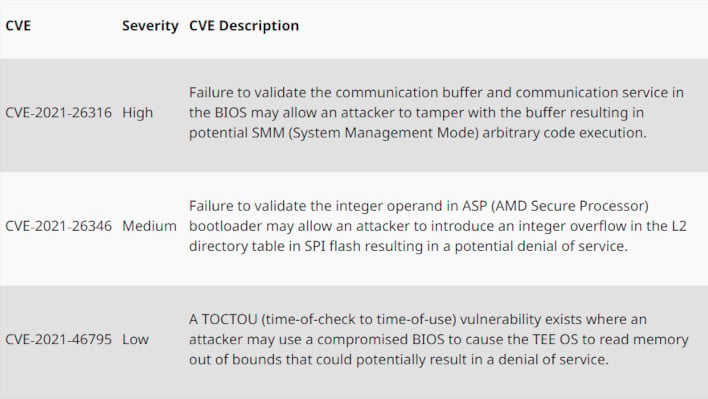
Vulnerabilities for AMD Desktop CPUs
Working with independent researchers, internal researchers, Apple, Oracle, and Google, AMD was able to publish new AGESA versions with mitigations for the vulnerability of many of the processors affected. However, it is up to vendors to deploy updates to a motherboard's BIOS with these fixes applied. We'd advise you keep an eye on your manufacturer's support page for updates to the BIOS if you have an affected CPU.
The list of vulnerabilities is quite long with a vast variety of severity and issues that would be patched, assuming a patch is necessary for the associated processor. The desktop options include Ryzen 2000 to Ryzen 5000 processors, Threadripper 2nd and 3rd generation, and the Athlon 3000 series. Mobile variants of these chips are similarly impacted.
On the server and data center end of the spectrum, the list of vulnerabilities includes first, second, and third-generation EPYC processors. Data center operators should work quickly to ensure affected systems are updated, assuming they have not already done so.
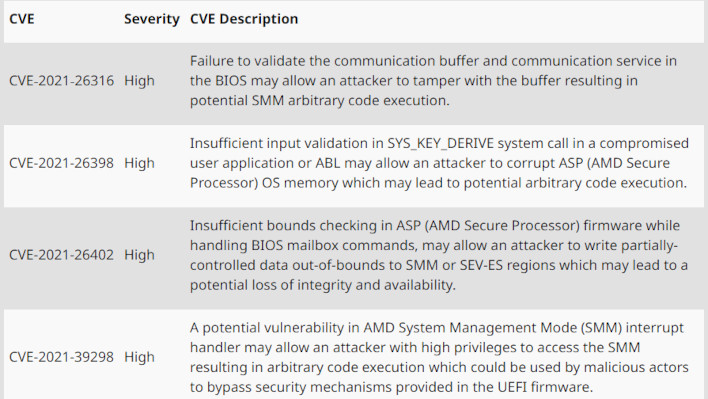
List of some AMD server and data center processor vulnerabilities
The full details on the data center and server processors can be read in this product security bulletin. The details for the desktop and mobile processors can be seen here. We do not anticipate these mitigations will have as much impact on performance as the Spectre and Meltdown patches did.

