Macros can be highly useful tools in Microsoft Office. Most Microsoft Office macros use Visual Basic for Applications (VBA) or Excel 4.0 macros (XLM). These programming and macro languages have a surprising amount of access to system resources on Windows machines, especially considering they only run from within
Microsoft Office. The benefit to these macros is to simplify complex functionality, such as automation in Microsoft Excel or field validation in forms that may have been integrated into a Microsoft Word document, to name a few.
Despite their usefulness, however, macros are often used to deploy malware as well, because they are capable of downloading and executing external software. Because most Office applications can integrate with each other, a macro can grab your Address book from Outlook, for example, and allow whatever malware you may have been infected to send malicious payloads to your contacts. Microsoft's dominance in the productivity and operating systems spaces has made their software rich targets for a very long time, with the angle of attack often bring macros.
Microsoft recently issued a patch to most newer versions of Microsoft Office
disabling macros if the Office file being opened was flagged as " downloaded from the internet." Initially the flag was automatic and turned on everywhere for all users. However, many small business users who rely on macros asked Microsoft to hold off on such broad sweeping changes, and so the
patch was rolled back, unfortunately
without much notice. Today system administrators have the ability to have the security flag for online macro detection turned on as a Group Policy, but it's not on for everyone by default. As such, macros can still be an attack vector, however, according to a
recent report by cybersecurity firm Proofpoint, malware and threat actors are searching for new attack vectors that may circumvent Microsoft's stricter security policies as they relate to macros.
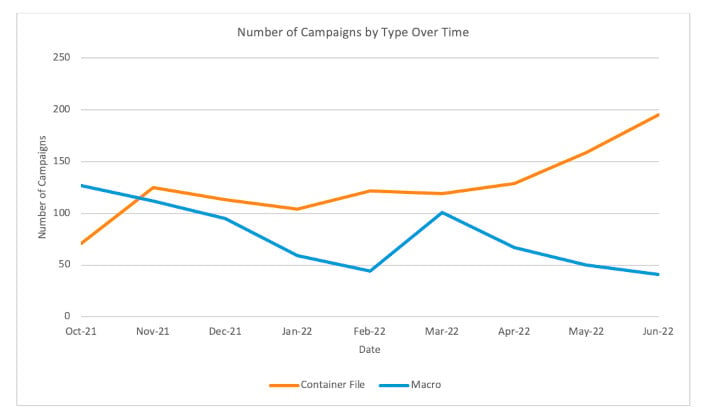
 Graph Showing Container Campaigns vs Macro Campaigns (Source: Proofpoint)
Graph Showing Container Campaigns vs Macro Campaigns (Source: Proofpoint)
How could they do it? By essentially forcing users to take an extra step when downloading attachments. If an Excel file is downloaded from a web browser, or as a direct attachment from an e-mail, it will be flagged as coming from the internet. However, if the file originated from inside a container-style file, such as a zip, rar, iso, img, or other container, the originating location will be the local drive according to Windows. Because the file was extracted from a compressed container, the "from the internet" flag isn't applied.
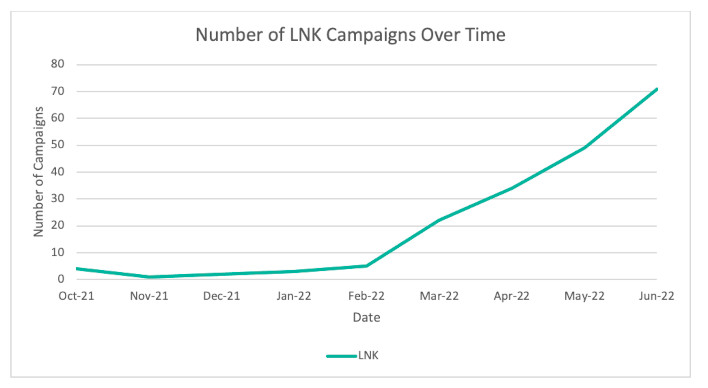
LNK files can also be used to circumvent Microsoft latest measures. On Windows machines, LNK files are used for things like desktop shortcuts. Less savvy users may click LNK files and be linked to a malware payload that might already reside locally, or even pushed into downloading malware. Proofpoint's statistics indicate that LNK based-threats have significantly increased since Microsoft's announcement to restrict the default behavior and use of macros.
 Graph Indicating an Increase in LNK malware campaigns (Source: Proofpoint)
Graph Indicating an Increase in LNK malware campaigns (Source: Proofpoint)
Regardless of the measures and potential restrictions put in place by Microsoft, security education and training remain a users best protection against malware. Never clicking links or opening files from untrusted sources is key. System administrators, of course, are advised to regularly remind and update users on best safety practices as well.